Overview
Yesterday, GE Digital published 2 advisories of vulnerabilities in GE’s SCADA/HMI product - Proficy CIMPLICITY that were discovered by OTORIO’s research team.
The two vulnerabilities are -
- CVE-2022-23921- Privilege Execution Vulnerability (CVSS - 7.5)
- CVE-2022-21798 - Credentials Vulnerability (CVSS - 7.5)
Why this is important:
GE Digital is a leading provider of industrial software solutions and IIoT services. As such, their systems can be found in almost every industry. The GE CIMPLICITY is a well known HMI/SCADA system with a well-established track record. Where installed, CIMPLICITY is typically the key component that controls and monitors the operations in the manufacturing environment.
Given CIMPLICITY’s central role in OT environments, the two vulnerabilities introduce a huge disruptive impact potential on this operational server. We can assume that if and when attackers establish a foothold in the network, CIMPLICITY will be on top of their list.
The Good News:
Interestingly, the two vulnerabilities announced by GE are totally “mitigatable“. If the server’s installation was done correctly and with security in mind, there is a good chance that they’re not exploitable (unfortunately, all too often this is not the case).
The OTORIO Research team addressed the issues in the past. If we look at CVE-2022-21798 for example, the default configuration of the affected CIMPLICITY servers is vulnerable and exposes sensitive information to the network. However, If configured correctly with the existing security features of the system, the risk is immediately mitigated. Our recommendations, along with an open-source hardening tool we designed can be found below or by using this link: https://github.com/otoriocyber/CIMPLICITY-Hardening-Tool
Mitigation Steps
- Run the OTORIO security verification free and open-source tool in order to get a summary of different issues in the CIMPLICITY ENVIRONMENT
- CVE-2022-23921- As GE stated - “ensure access to the CIMPLICITY machines and directories are properly controlled via Access Control Limits (ACLs).” - specifically to the directory where the runtime project of the CIMPLICITY is stored.
- CVE-2022-21798 - If possible, follow the SDG guidelines of how to set up IPSEC communication between all CIMPLICITY nodes. If not possible, it is recommended to use secure sockets that are easily configured from the CIMPLICITY Options panel -
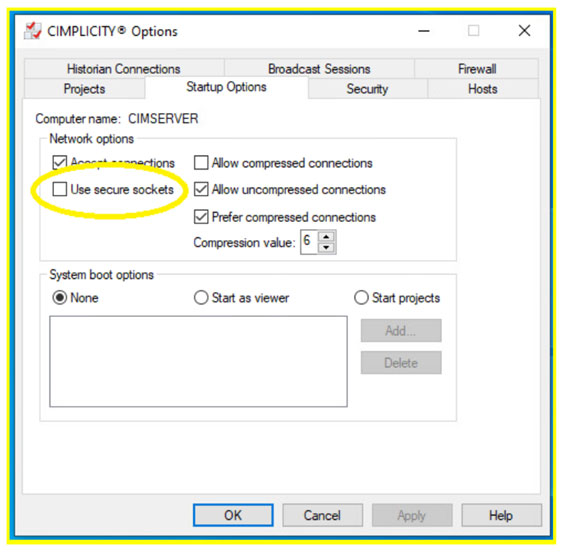
- It is recommended to update the CIMPLICITY system to its latest version - released January 7, 2022.
Acknowledgements
A recognized global leader, GE Digital takes the security of their products seriously and applies time and resources to ensure its customers remain safe. We were truly impressed by the incredible engagement and collaboration of the GE team throughout the process. We also want to thank GE for endorsing OTORIO’s hardening tool in the Advisory itself. It is not trivial to get this kind of support from such a market leader.
For any question or suggestion regarding the vulnerabilities or security measures, feel free to contact us at -
Recent Posts