By Younes Dragoni, Director of Business of Development & Technology Alliances
Critical infrastructure found itself on shaky cyber-footing long before Russia invaded Ukraine this past February. Since at least 2016, Russian hackers have penetrated the U.S. power grid, according to CISA, and put the world on notice that energy plants and operations are not safe from attacks on IT and OT systems. Today, more than four months after Russia launched its war against Ukraine, the Oil and Gas industry finds itself in a precarious position as it hopes to avoid potential Russian cyber attacks.
For decades European countries have depended on a cheap, steady supply of liquid natural gas (LNG) coming from Russia. In 2021, the country supplied over 40% of the E.U.’s gas, however, Russia and its majority state-owned Gazprom created an artificial tightness in Europe’s gas market by cutting supplies to the region by 25% in the fourth quarter of 2021.
At the beginning of 2022, Russian LNG flows to Europe slowed to a trickle, falling by 37%. In April, Russia cut off gas supplies to Poland and Bulgaria. A month later, it stopped all LNG exports to Finland.
On July 11, Russia stopped LNG flows into Germany through the Nord Stream pipeline for ten days of scheduled maintenance. It remains unclear whether LNG flows will resume when maintenance is done. For a country that imports more than a third of its gas supply from Russia, the potential impact this could have on Germany’s economy is significant. Experts believe that a total shutdown of the Nord Stream gas pipeline to Europe via Germany is “not inconceivable.”
LNG supply chain instability has wreaked havoc with prices, showing how vulnerable European countries, manufacturers, and consumers are to shifts and disruptions in the market.
Unfortunately, Russia’s impact on energy activities will not likely end such supply chain interruptions. The country's reputation as a nation-state sponsor of cyber attacks makes it likely that Russia and threat actors supporting it will turn their attention to hacking European gas storage and processing plants that it once filled. Additionally, LNG suppliers and refineries worldwide who are helping Europe make up for its supply chain shortfall are also likely to be at increased risk.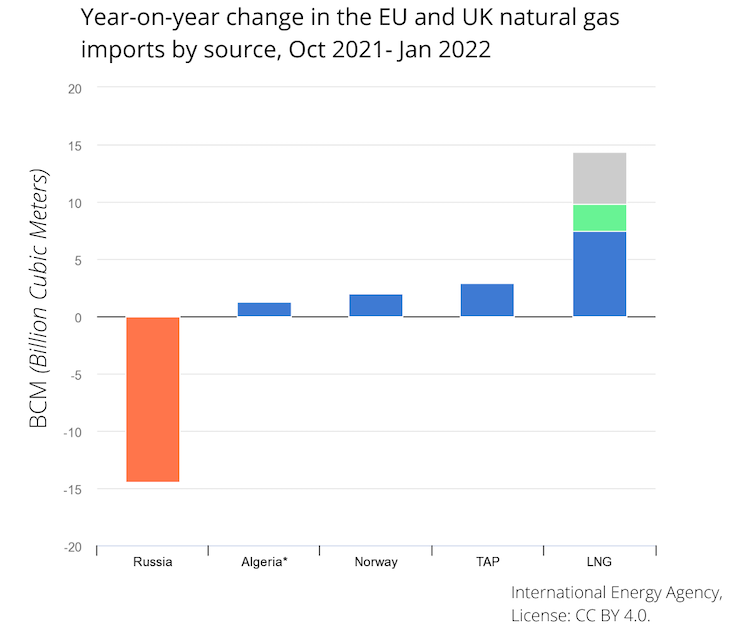
Refilling Europe’s LNG Supply
In light of these Russian-initiated supply chain disruptions, the U.S., Qatar, Algeria, and others are stepping in to ensure that Europe has a sufficient supply of LNG for the winter. The region’s reserves and an unseasonably warm 2022 winter enabled the E.U. to get through the first half of this year reasonably unscathed.
Some countries, including Italy, are reaching out to alternative energy suppliers. This year, Italy reduced its reliance on Russian oil imports from 40% to 25%, turning to Algeria to make up the difference.
However, European manufacturers are bracing for winter without Russian oil. The Wall Street Journal reported that Yara, an ammonia producer that relies on NLG for production, has had to ramp down production due to sharp gas price increases. Aurubis AG, one of Europe’s largest copper suppliers, is looking to substitute gas with electricity.
Glass producers, galvanized steel manufacturers, and automotive plants are just three industries that are oil-dependent. A gas shortage could lead to manufacturing delays, factory shutdowns, and new supply chain shortages.
A History of Attacks
If Russia turns its attention to cyber attacks against LNG targets, it would not be the first time. Russian digital intrusions against Western energy supply companies date back at least a decade.
In March 2022, the U.S. Department of Justice publicized two criminal indictments that it filed against Russian military officers, accusing them of attacks dating back to 2012. The alleged cyber attacks against critical infrastructure included reported hacks and malware installations against a nuclear power plant in Kansas, and scores of oil and gas firms, utilities, and power transmission companies.
In the two weeks leading up to the invasion of Ukraine, Russian hackers were reportedly focused on cyber attacks against LNG companies. According to Bloomberg and Resecurity, more than 21 such refineries, suppliers, and distributors were attacked during a 2-week ‘pre-positioning’ blitz before the war began in February. U.S.-based LNG-related companies that were allegedly targeted included Chevron, Kinder Morgan, Cheniere Energy, and EQT Corp.
And then there is Colonial Pipeline, one of the biggest pipelines in the eastern United States. It moves gas north from southern Texas to New Jersey, supplying home heating oil, automobile gasoline, and jet fuel for the East Coast.
In May 2021, Russian-based cyber criminals accessed the system. They stole data and then infected its digital systems with ransomware. The pipeline was shut down for five days while Colonial Pipeline paid the ransom and cleaned out its system. Although the U.S emphasized that Russia itself did not conduct this particular cyber attack, but rather it was done by private, Russian-based criminal hackers, the U.S. Cybersecurity Infrastructure Security Agency (CISA) continues issuing regular advisories about the potential for malicious cyber activity by Russia.
As the war drags on in Ukraine, Russia is seen as more likely to lash out as economic sanctions and efforts to decrease reliance upon Gazprom’s LNG pipelines continue. Considering its willingness to interfere with the world’s LNG supply, as well as its past history of targeted attacks against critical infrastructure, many experts are concerned that LNG producers remain at high risk for Russian-sponsored industrial cyber attacks.
Neal Higgens, deputy national cyber director for national security in the United States, recently told attendees at a defense event, "A slow military progress continues to thwart the Russians on the ground in Ukraine. They may increasingly consider cyber options to divide our allies and to dilute international resolve against its action."
Europe's LNG Supply and OT Security
Current events are pushing European nations to end their dependency on Russian energy. The supply slowdowns last year, and this year's pipeline shutdowns have convinced the E.U. to walk away from cheap Russian LNG and oil supplies.
However, taking this stand against Russia could put LNG, oil, and gas companies at much greater risk for OT security attacks against their facilities. Russia and third parties acting on its behalf allegedly demonstrated their ability to access foreign LNG businesses and their networks. They use a combination of hacking techniques and social engineering, including trying to offer former employees $15,000 on the dark web for credentials to access networks of refineries and distributors where they no longer work.
Any oil and gas company that takes LNG security seriously must consider these actions as imminent threats to their business and production operations. Reducing digital vulnerabilities, and implementing oil and gas cybersecurity measures is critically important to reducing risks against cyber attacks.
Protecting OT Security
Russia is likely to be focusing its attention on LNG companies helping Europe make up for its corresponding shortfall in Russian-supplied gas, with the potential to target countries that support Ukraine during the war. Oil and Gas companies must vigilantly practice digital risk management to keep their OT-IT-IIoT network environments secure.
Russia’s ongoing activities affecting the world's energy supply chain should have CISOs, SOC teams, and other oil and gas industry professionals think about enhancing their security posture. Implementing an end-to-end OT security solution helps protect business continuity and ongoing production. LNG refineries and suppliers are already moving to strengthen their OT security and OT-IT-IIoT networks to proactively mitigate the risk of cyber attacks by nation-state actors and third parties acting on their behalf.
Taking proactive steps today, before an attack comes, provides refineries, distributors, and suppliers a better and more informed ability to repel attacks. Today’s OT-IT-IIoT networks are deeply intertwined, and industrial manufacturers rely on them to produce the energy needed by end-users. Securing the entire perimeter should be a top priority for the sector.
Those who question whether Russia has the audacity to support cyber attacks against the LNG industry in Europe and around the world need only look at the way it has already been accused of doing so against critical infrastructure companies in the U.S.
If you are an Oil & Gas industry professional interested in assessing OT-IT security network risks and strengthening your company’s security posture, contact us today so that we can discuss your situation.
Recent Posts