Project Files are the Blueprints of the Industrial Processes
Project files hold the organization's most sensitive know-how including information about different network configuration mapping, hardware and software configurations, screen definitions, and the actual automation logic of the controllers.
Normally, project files are kept encrypted in a digital vault. However, because of the growing need to collaborate and share information with suppliers, for example, they are transferred unencrypted via the internet. Once they reach the wrong hands, they could be used as a map for a targeted attack and potentially create massive damage to production.
In recent years scanning incoming files for malicious attacks using online scanning services has become a common practice amongst most companies and organizations worldwide – an effective work method that hasn’t skipped the industrial sector as well.
In order to facilitate the process, certain security tools upload and scan files online automatically. This casual and seemingly everyday action was found by OTORIO’s research team to have resulted more than occasionally, in the uploading of highly sensitive business information or intellectual property which in most cases remain online to be accessed by analysts in the larger cyber community.
Top Secret Project Files On-demand
OTORIO’s team was looking for infected Industrial project files, like the ones the Stuxnet malware used as its propagation method. The research was conducted on one of the leading scanning engines available today, Alphabet’s Virustotal, but this flaw is occurring on other online scanning engines, as well.
Thousands of project files belonging to dozens of industrial companies and vendors from different verticals and geographical regions were identified by the research team. Some project files belong to the largest Automotive (OEMs), Consumer Goods, Food & Beverage, and Electronics manufacturers in the world.
The extent and diversity of the data that was found to be uploaded, indicates a serious systemic problem in the process of handling and scanning sensitive information by the industrial sector. To be precise, the systematic flaw in the process does not lie in the use of Virustotal’s scanning engine, but rather the unintentional upload of project files to Virustotal.
Production Blueprints as Powerful Cyber-weapons
Although project files remain online indefinitely, they can only be accessed for a limited time of up to 12 months, and the information can be accessed only by licensed cyber-security researchers. Nonetheless, in order to enable fast and efficient use, the online scanning engine providers cannot conduct an in-depth screening process for each analyst, thus potentially allowing rogue players access to the scanners’ database and confidential information such as those said project files.
The project files, being the blueprint of the production floor/ automation process/machine, usually consist of hardware and network configurations and may also contain the actual automation logic. Access to such files can potentially turn even a well-guarded company into an easy target for a sustainable cyber-attack. This type of information is extremely helpful when designing a targeted hack into production floors. It could dramatically simplify the desired hack, hence, making a successful cyber-attack on a production floor accessible for a larger malintent player or community.
Cybercriminals can use the information embedded in the project files to identify a potential supply chain attack vector or alternative entry points used for remote maintenance, monitoring or operations.
The most familiar recent attack is the Hydro Norsk cyber incident resulting in a global disruption to their manufacturing capability. Also, in 2014, a German steel mill was the target of a cyberattack when hackers successfully took control of the production software and caused significant material damage to the site.
What Can be Done?
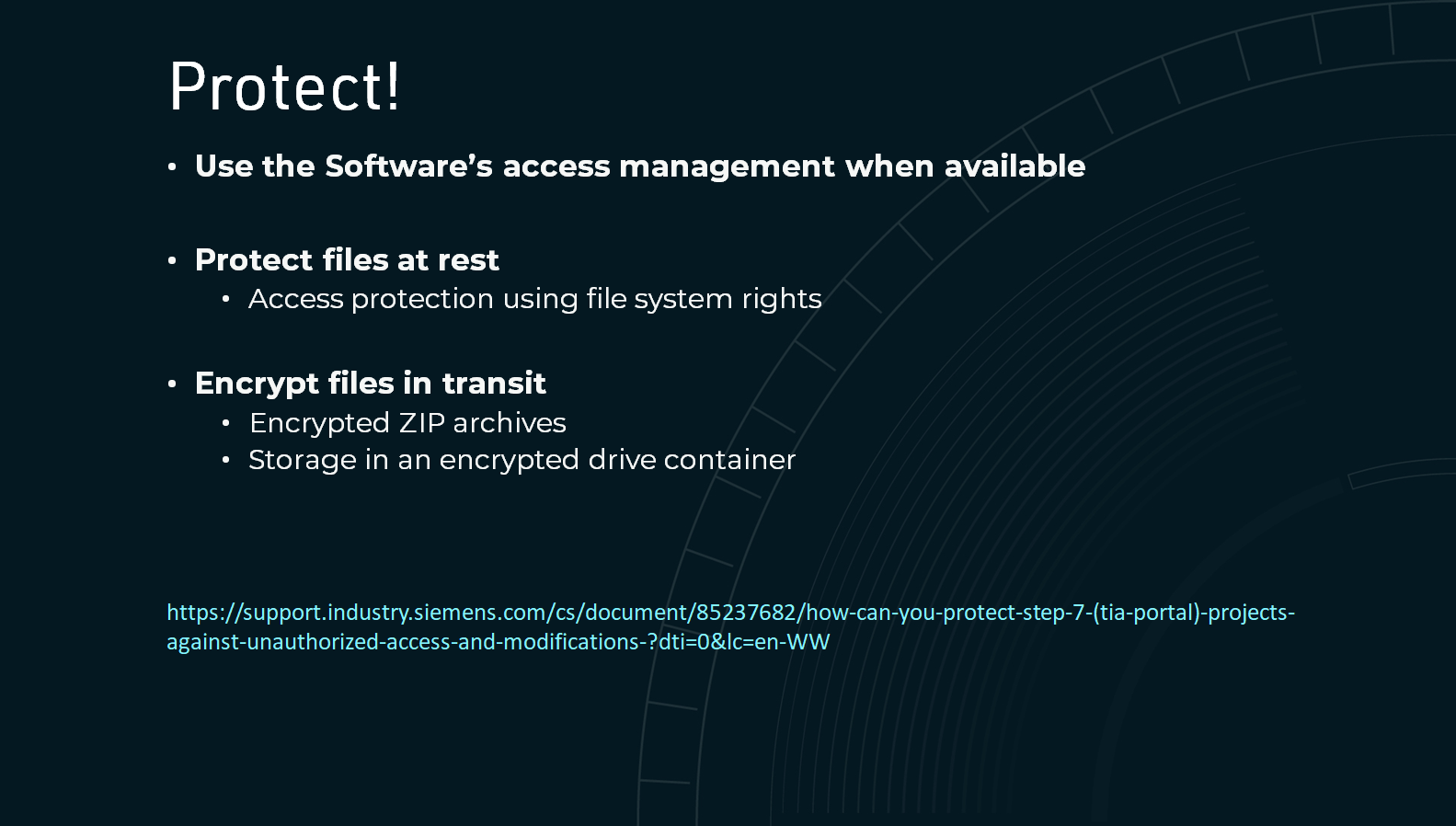
Configure!
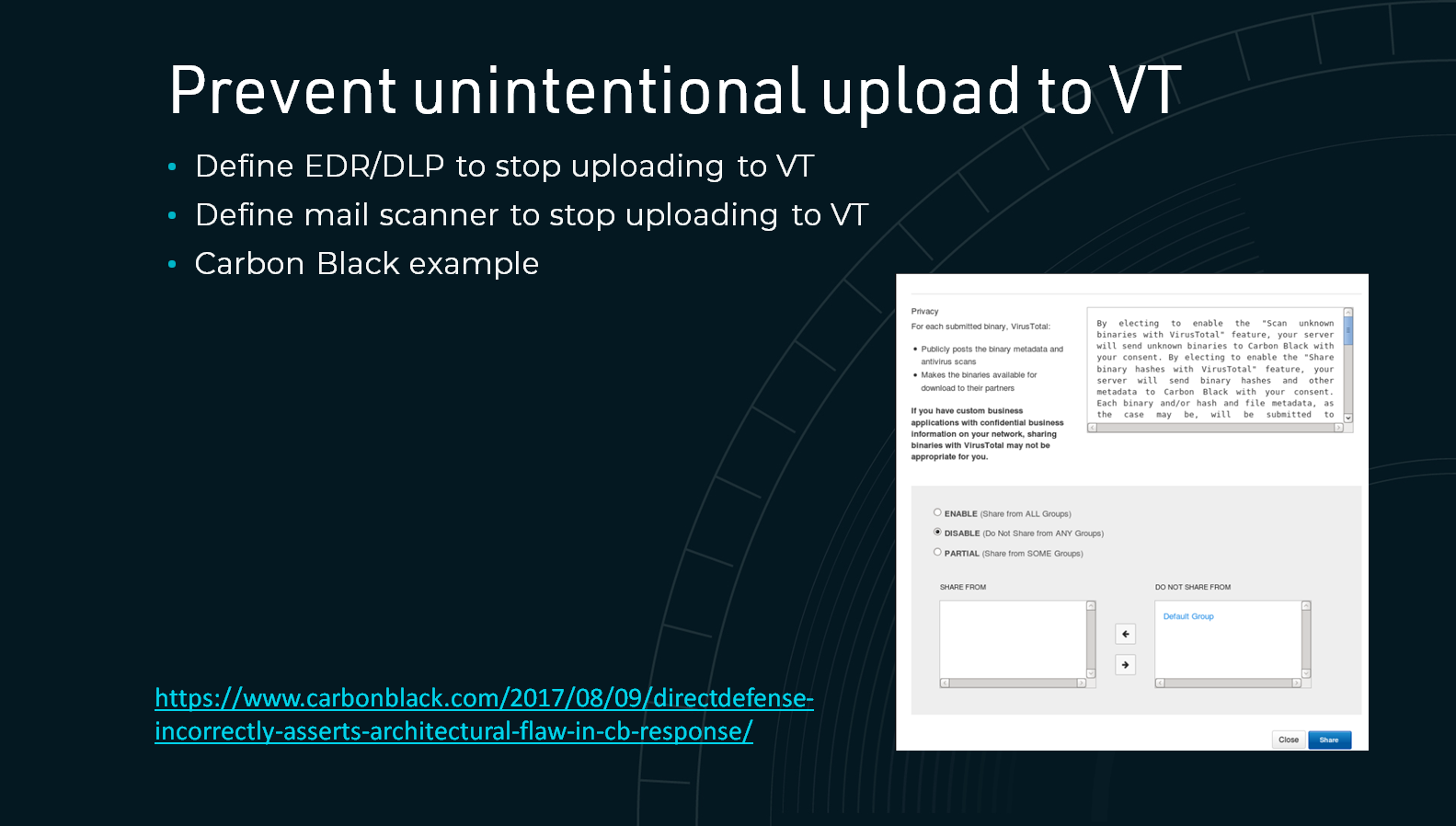
While some of the information has been uploaded via 3rd party automated email gateway scanners, others were most likely uploaded via inhouse EDRs, DLPs or IDSs. To avoid the problem, the processes that are connected to online services should be evaluated and properly configured.
It is important to clarify that uploading the project files was not done deliberately by industrial companies, vendors or security service providers, rather they were uploaded unintentionally and automatically because of misconfigurations in the security applications that rely on online scanning engines to test for malicious files.
Raise Awareness
OTORIO’s team contacted Virustotal and shared its findings with the company. We were pleased to learn that Virustotal shares our concerns regarding the way industrial companies mishandle their API’s configuration and the need for raising awareness of the problem.
The importance of the topic has led to it receive global media coverage in business and technological newspapers.
This summary merely scratches the surface of a much deeper matter that requires the industrial sector’s utmost attention. OTORIO presented this topic at CS3 conference in Stockholm, Sweden in October 2019, including proper ways manufacturers can better protect themselves and use online scanning services more wisely. Here are two slides that were presented during the conference.
For questions and additional information regarding the research, reach out to our team.
Recent Posts