An ICS-Cert advisory was issued last week by OSIsoft, a leading operational software vendor.
In the advisory, OSIsoft reported a vulnerability that affects their PI System, a data management platform that accesses a broad range of core OT network assets in its sites.
PI System runs and manages many of the world's most critical infrastructures. Installed in over 19,000 industrial sites in 107 countries worldwide, the system is used by 15 of 16 sectors of US critical infrastructure as defined by a United States Presidential Policy Directive.
The PI System collects, stores, and organizes data from all plant data sources and is accessed by company operators, engineers, managers, and other plant personnel. They retrieve data from it via various human-machine interfaces (HMIs) and client side applications, some of them utilizing the PI Web API.
This vulnerability, which could have had massive implications if exploited, was discovered by the OTORIO Incident Response (IR) team.
The incident was given a score of 7.7 on the Common Vulnerability Scoring System (CVSS), a software vulnerability metric which runs from 0 to 10. A score of 7 or more denotes a high severity risk to company assets and indicates a high priority for immediate mitigation. OSIsoft suggested that their users upgrade to PI Web API 2019 SP1.
Step-by-Step, Real Life Attack Scenario
The discovered vulnerability, if exploited, could enable attackers to run client-side code on client browsers and deceive users into providing their credentials to attackers. The exploit is implemented when a user passes the cursor over an infected field in the PI System.
OTORIO created a short video illustrating the vulnerability which you can view below.
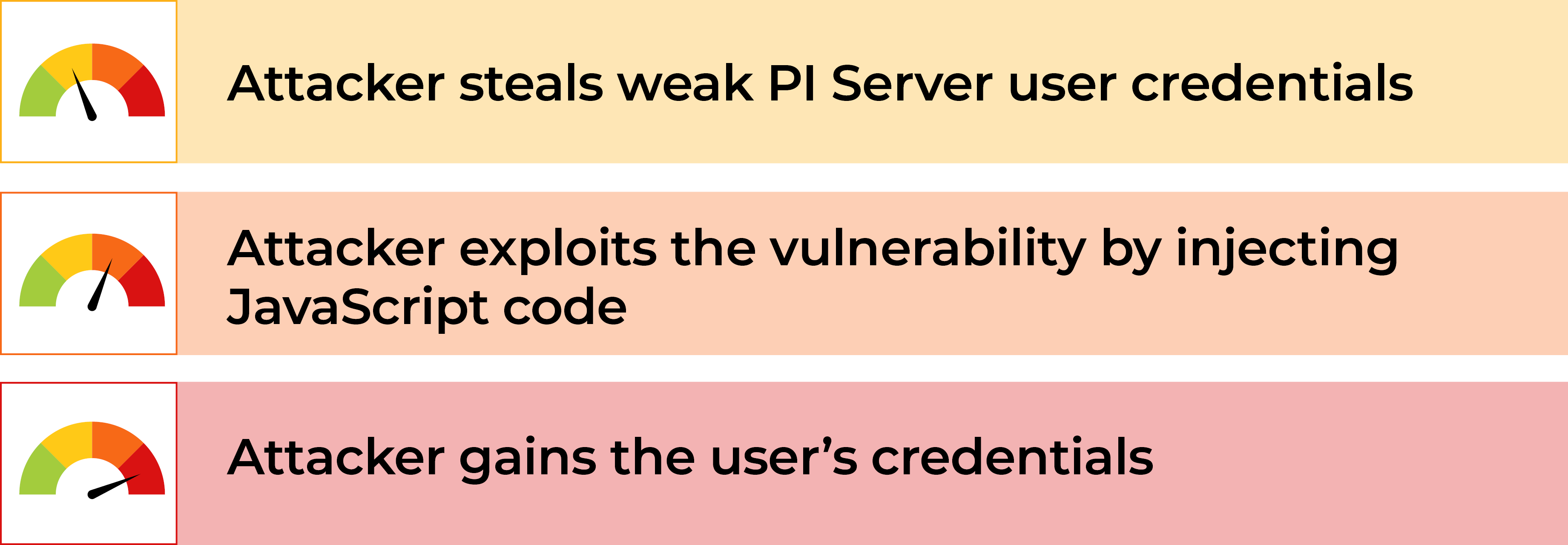
How would this vulnerability be played out in a real life scenario?
- An attacker steals weak PI Server user credentials (or convinces an insider to insert a specific string to certain PI Server fields).
- The attacker exploits the vulnerability by injecting JavaScript code into the vulnerable fields in the PI Server
- Once a user with high privileges uses the PI Web API and passes his or her cursor (mouseover) over the infected fields, the attacker gains the user's credentials.
Why Should You Care?
At this point, an attacker with the user’s credentials at hand can wreak havoc on the PI System at any location running their software.
Here are some ways exploiting the vulnerability can cause damage:
- Change the data that comes from plant data sources. This could, for example, cause operators and engineers to think that the temperature of a boiler is higher or lower than it actually is. This could cause damage to property - and even worse - to people in the vicinity.
- Delete historical plant data.
- Implement web page keylogging, auto-redirect, steal cookies, change infected page data, steal browser information, and more.
- If the attacker has high credentials, s/he can gain access to the production floor and potentially alter component and machinery attributes.
After an attacker gains access to production floor machinery, OT professionals have to immediately assess and isolate the vulnerability. As part of their assessment, they need to know:
- Is the attack an isolated incident relegated to one location?
- Is the attacker capable of threatening other company locations?
OSIsoft's Immediate Response
The vulnerability affects the PI System’s PI Web API 2019 version 1.12.0.6346, and all previous versions. OSIsoft immediately issued a knowledge base article and an update for customers.
Moving Forward
This vulnerability was found and mitigated before it was exploited. Other critical infrastructure systems may have undiscovered vulnerabilities which might threaten their systems. For additional information about securing your industrial operation, contact us.
Recent Posts