https://www.otorio.com/remot-secure-remote-access/
By OTORIO Research Team Leader Eran Jacob

License to Breach: RCE Affecting Siemens Servers Including PCS 7, Historian, WinCC, and Engineering Servers
Recent findings by our team have uncovered two vulnerabilities in the Siemens Automation License Manager (ALM), a license management service used to control and manage the usage of Siemens’ industrial automation products (CVE-2022-43513 and CVE-2022-43514). The discovered vulnerabilities, chained together, allow remote code execution (RCE) and privilege escalation (PE) on the affected systems, which allow an attacker to gain unauthorized access to the system with elevated privileges.
The impact of these vulnerabilities is significant, as they can be used to disrupt the normal operation of industrial systems and cause severe damage. The vulnerabilities affect a wide range of Siemens’ products, including PCS 7 Historian, WinCC, TIA Portal, DIGSI, SICAM Device Manager, and others. These products are widely used in various industries such as manufacturing, oil and gas, energy, and smart transportation.
Learn how OTORIO's oil and gas cybersecurity solution ensures operational continuity.
The PCS 7, for example, is one of the most common DCS solutions. It plays a critical role in supervising normal operations on the industrial shop floor and by design, has high privileges on the entire process.
Even though Siemens did not detail all of the affected products (at the time of writing this paper), we found that most of the modern applications of Siemens use the ALM as the license manager, built-in, without the option for an alternative, as can be found in the following examples of Historian and OS-Server (PCS 7 core components) installation.
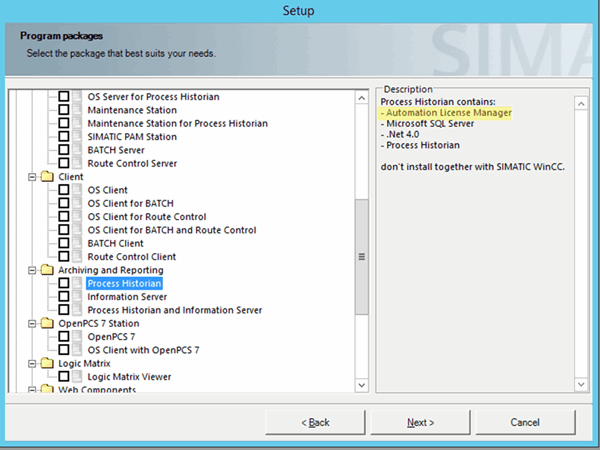
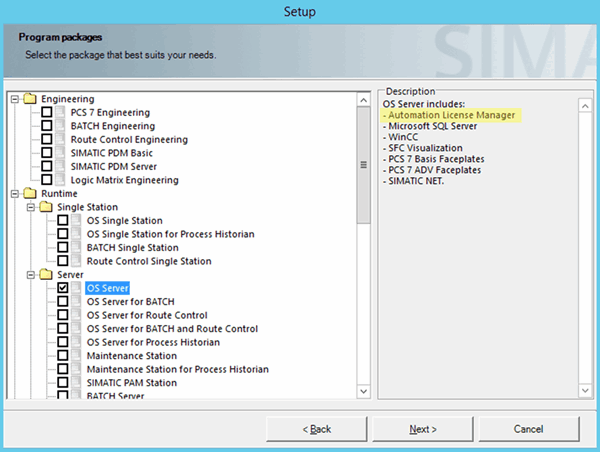
PCS7 Installation: Automation License Manager installed automatically on all servers
One of the most concerning aspects of these vulnerabilities is that they can be used to breach industrial control systems (ICS) from almost any entry point in the network: once an attacker has access to the OT DMZ, even with weak permissions - one can fully compromise the OT network by executing privileged code on the control system, and by that overcoming the segmentation & access control of the network.
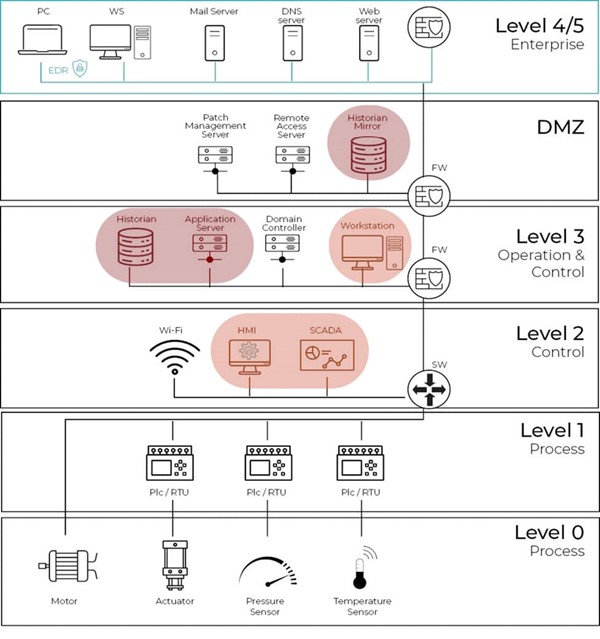 Illustration of the vulnerable machines through the different Purdue levels
Illustration of the vulnerable machines through the different Purdue levels
For example, the PCS 7 Historian, which is used as a repository for industrial process data, can be used as a ‘bridge’ for an attacker to propagate from the corporate network into the OT network. Once an attacker breaches the Historian server, one can potentially gain access to engineering, control, and monitoring systems.
An attack could take place not only from the Enterprise network. For example, any compromised station with minimal privileges in the network, such as a thin client computer that has access to one of the Siemens servers, could lead to a full compromise of the network.
In the following Illustration, two attack scenarios aim for the OS-Server as the end goal (As the OS-Server is a critical and highly privileged server within a PCS 7 environment). The first Enterprise-level attacker is able to compromise the Historian server in the DMZ and then reach the OS-Server with a second hop. The Control level attacker can use the vulnerabilities to elevate privileges and have full control over the control system.
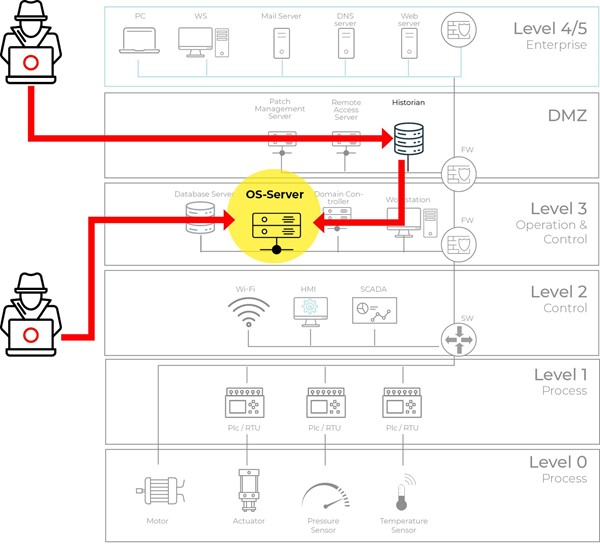 Illustration of the two attack scenarios
Illustration of the two attack scenarios
According to Eran Jacob, a research team leader in OTORIO, "The described control systems are some of the most privileged servers in the OT network, and by that are high-interest targets for attackers. Exploiting these vulnerabilities can lead to severe impact on industrial and critical environments."
Siemens has taken steps to address these vulnerabilities, and customers are advised to update their systems. Additionally, implementing robust security measures, such as blocking unnecessary ports, can reduce the risk of unauthorized access and potential damage to industrial and critical environments.
Additional mitigations to these vulnerabilities include:
- Limiting remote access to port 4410/TCP on all affected servers
- Disabling the remote license management feature in the ALM UI, unless required
- Updating the ALM service to the newest version (ALM V6.0 SP9 Upd4 or later version)
a. This is recommended in any case, since it is the only way to avoid Local Privilege Escalation risk. (https://support.industry.siemens.com/cs/ww/en/view/114358/)
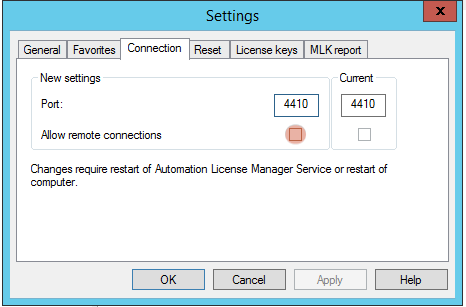 Disable remote access to Siemens ALM to avoid RCE
Disable remote access to Siemens ALM to avoid RCE
For OTORIO customers, OTORIO recommends customers use its platform to gain full visibility of the installed programs on Siemens servers in the network. Utilize the data collection capabilities of the platform, including SCM (Secure Compliant Machinery Windows Tool) and Safe Active Query, to obtain complete information on the installed software versions. Follow the platform's alerts identifying potential vulnerabilities and exposures, and the suggested mitigation steps for reducing risk.
CISA and Siemens have issued advisories regarding these vulnerabilities, which can be found at the following links:
- https://www.cisa.gov/uscert/ics/advisories/icsa-23-012-10
- https://cert-portal.siemens.com/productcert/pdf/ssa-476715.pdf
Note - Our current assumption is that full exploitation is possible on the default configuration of Windows-Server machines and might require specific configuration on desktop/embedded ones.
In conclusion, discovering these vulnerabilities in Automation License Manager highlights the importance of keeping industrial systems updated and secure. Asset owners should make sure they are aware of the SBOM in their environment - even if the vendor itself develops it. Comprehensive Asset Inventory and OT Vulnerability Management solutions can assist with unveiling vulnerable products and affected assets in their environment.
Recent Posts