Today we are releasing a new Windows hardening tool for one of the most commonly used HMI/SCADA systems: GE Digital’s CIMPLICITY. Over the past several months OTORIO’s researchers worked closely with GE Digital engineers. We embedded their feedback and insights into our work, and together, made sure the checks performed by our tool are aligned with GE's recommendations.
Why You Should Care:
GE Digital is a leading provider of industrial software solutions and IIoT services. As such, their systems can be found in almost every industry.
CIMPLICITY is a well known HMI/SCADA system with a well-established track record. This scalable automation platform provides visualization and control for industrial systems of various sizes and architectures. Where installed, CIMPLICITY is the key component that controls and monitors the operations in the manufacturing environment.
From a more technical perspective, CIMPLICITY is a versatile software application that can run on a single server or in a variety of client/server architectures. A typical deployment includes a CIMPLICITY server, CIMPLICITY clients (often used as HMIs), Engineering workstations, and a Proficy Historian. Each one of those has a critical role in the proper functioning of the network.
GE Digital and its customers share security responsibility. Moreover, GE Digital invests a lot of effort into the security of CIMPLICITY and its deployment guides. But making complicated systems secure is not an easy task. In a complex industrial environment, there are a lot of connections and data flows between different layers of the factory, as can be seen in diagram 1 below. Hence, automate parts of the process and adding one more layer of verification can significantly improve a company's security posture.
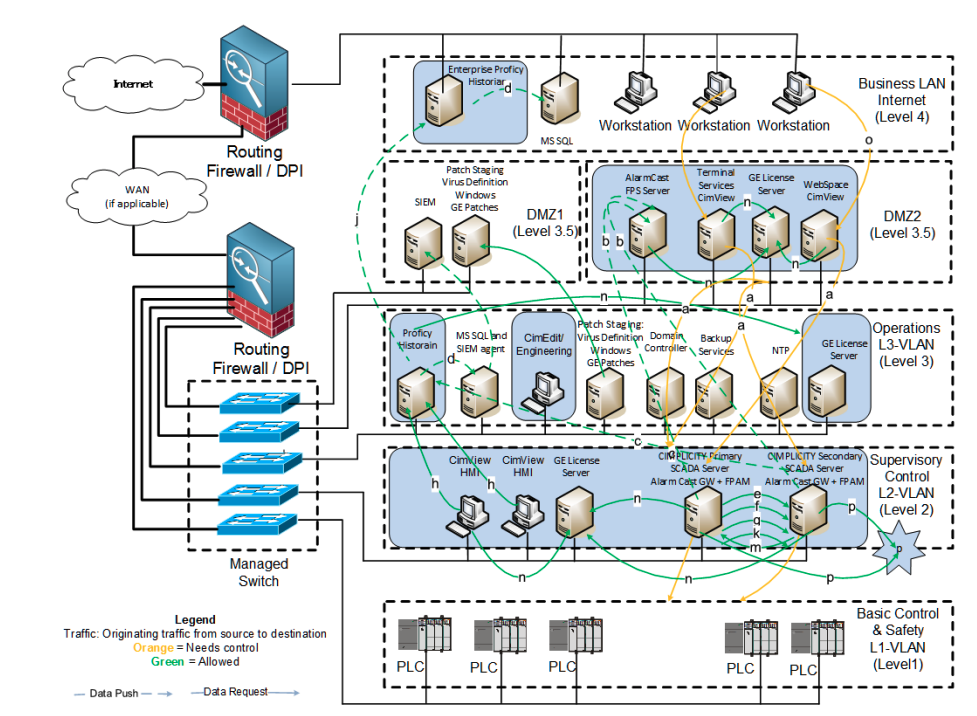
Diagram 1 - Remote access to CIMPLICITY screens (source: GE CIMPLICITY HMI/SCADA - SECURE DEPLOYMENT GUIDE)
Hardening CIMPLICITY
The purpose of the tool OTORIO is sharing today is to verify the security configuration of the Windows machines of the different CIMPLICITY components. It contains 16 OT security insights, based on dozens of Windows checks that are derived directly from GE’s security recommendations. Its goal is to verify that the installation of CIMPLICITY was is done in a secure environment. We are also recommending users run an annual test to make sure that the system stays secure over time.
A Simplified Process for the Non-Cyber-expert User
Cybersecurity experts are seldom present on the production floor. Therefore, we designed the tool with the system integrators who install these systems and OT security personnel within the plants as its primary users. The tool is as simple as a “double click” of a PowerShell script, which makes it easy to run even for non-technical personnel.
It’s important to note that we are not proposing that the new tool addresses all the possible misconfigurations or that it checks all of the security flaws that may arise in CIMPLICITY environments (like network segmentation of the network for example). GE Digital's model assigns responsibility and liability to the buyer or user (see Disclaimer of Warranties and Liability in the secure deployment guide) yet it is committed to continued collaboration on security. We believe that this tool provides an effective way to verify the control servers themselves, and is definitely a good starting point.
Importantly, we would like to thank GE Digital for their cooperation and feedback of the tool. We hope that more automation vendors will follow GE’s example and join us to take an active role in securing their systems.
Get the CIMPLICITY hardening tool from our Github
Important Note
CIMPLICITY is a trademark of GE. OTORIO is not owned or affiliated with CIMPLICITY, GE Digital, its affiliates or subsidiaries. The Open Source tool was developed is and being offered solely by OTORIO.
For any questions, suggestions, or feedback, feel free to reach us at-
Get a Cyber Assessment
Recent Posts