Industrial Darwinism
Digitalization is rapidly transforming the way industries operate. In this constantly evolving economy, digital-driven growth empowers new business opportunities, dramatically affecting profitability by increasing productivity, effectiveness, and efficiency of operations. Businesses that do not adapt to the digital environment, lose competitiveness and risk becoming obsolete.
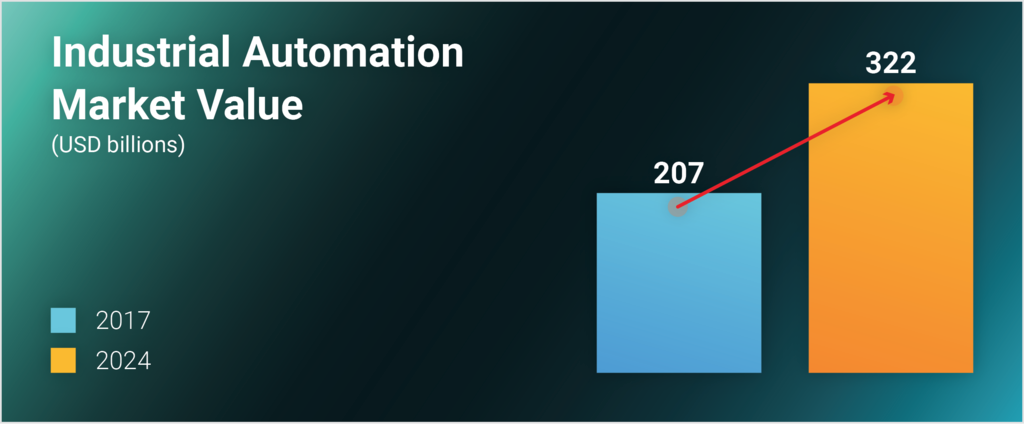
By the end of 2024, the global industrial automation market value is projected to grow by 35% in spending (source: Zion Market Research)
On top of the inherent operational challenges associated with digital transformation, industrial cybersecurity has become a major obstacle facing the industry today. The journey towards industrial digitalization introduces new cyber threats due to various reasons, the main being the structural differences between the IT and OT layers, that are becoming increasingly connected.
IT-OT Convergence
The industrial OT environment has developed considerably over the past years, resulting in a closely coupled IT-OT convergence. More and more enterprise IT systems like ERP connect to OT management systems, used to monitor and control the industrial operations (e.g. SCADA). The two technologies have evolved in a different way over the past years and require different methods of security.
IT rapidly and dramatically changed the fundamental structure of the enterprise technology environment. On-premise data centers were secured like medieval fortresses not too long ago, yet they are nowadays migrating to online-only cloud-based environments. The short periods between IT generations, plus the ever-growing cyber risks, have resulted in an almost homogenous IT environment (theoretically), immediately patched in an ongoing process.
On the other hand, the OT environment has evolved in longer processes, resulting in multigenerational, inherently insecure technologies. Because the OT devices were designed to operate in an air-gapped environment, no regular updates were available between the old and new equipment. The few security processes that do exist rely on manual operations, which are not only costly but also exhausting, ineffective, and slow to respond.
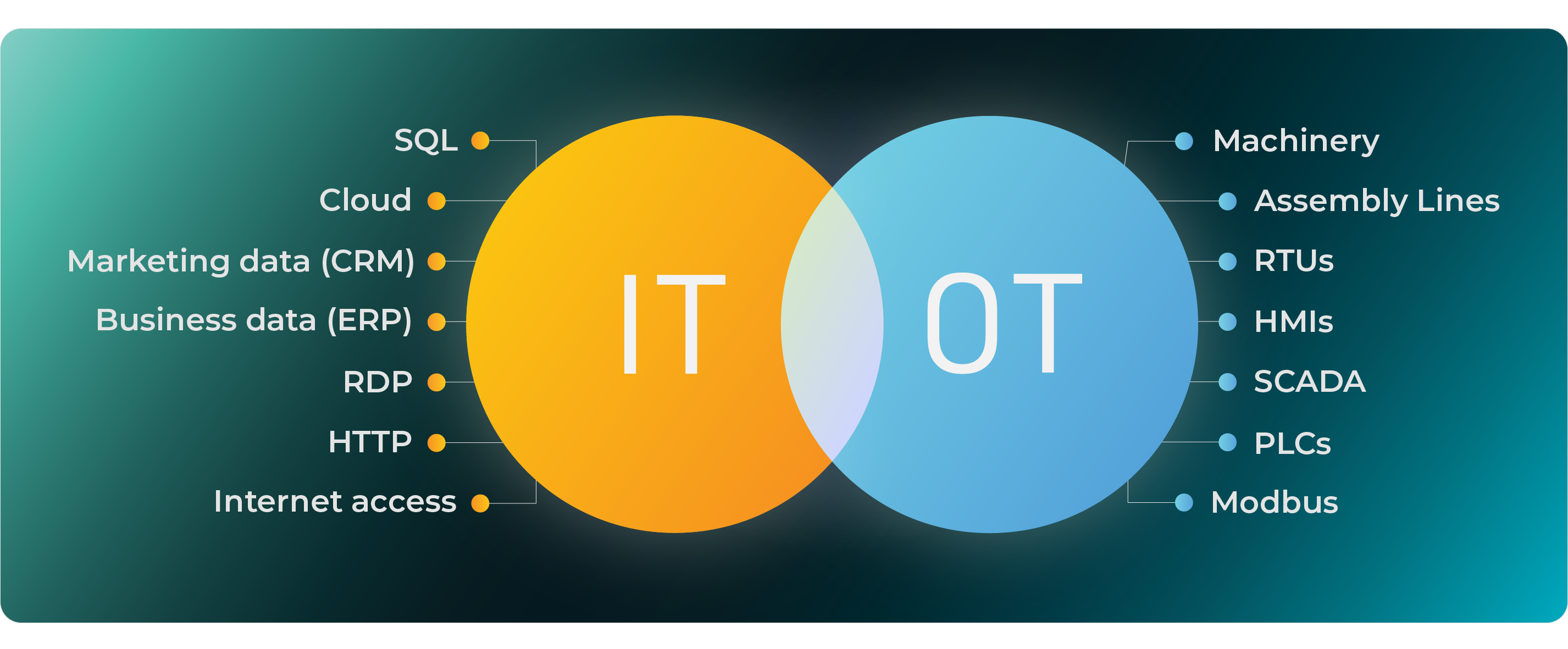
Most existing IT security solutions are not compatible with the inherent uniqueness of the OT environment, making IT/OT cyber risk management more challenging than ever. OT Risk management is crucial for safe digital transformation, especially in the face of an increasingly destructive threat landscape, where the assurance of safety, reliability, and productivity are at least as important to industrial business as the confidentiality of data.
By connecting physical to digital systems, the digitalization process expands the attack surface and increases the attractiveness for cybercriminals looking for new ways to monetize crime and interrupt business operations.
The Proliferation of a Destructive Threat
Until recently, it was the common belief that air-gapped solutions for production floors were effective enough to prevent IT-related malware from interfering with the operational industrial process. It was also believed that the existence of OT-related malware was not a likely scenario.
The past decade nevertheless introduced a new era of a global cyber arms race, illustrating not only their destructive potential but also their imminent risk to the digital industry.
A short recap of the world’s most significant cyber-attacks on industrial systems:
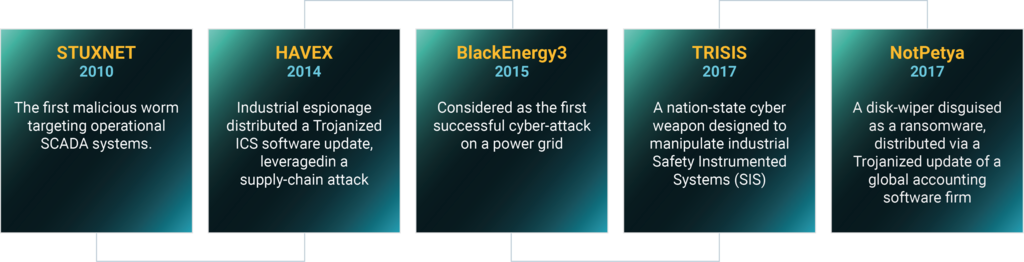
As attackers are improving their ability to bypass traditional blocking and prevention security technologies, production floors are exposed to upcoming cyber threats, having almost no preventive risk-reducing processes and strategies.
It is time to rethink the approach to industrial OT cyber security.
Embracing a Forward-looking Approach:
The Five Essentials for Safe Digitalization
The particularity of industrial operations calls for a paradigmatically different cyber risk management approach; one that will be synergistic with digital automation solutions, customized to the industrial-organizational DNA, and able to proactively counteract threats before they turn into vulnerabilities.
1. Preventive risk mitigation
As mentioned, OT was not, and still is not, developed with inherent security and patching capabilities. Some of the standard instructions for OT may even lead to intentional or unintentional physical damage, production failure, or disturbance (e.g., WannaCry).
Moreover, most OT cybersecurity products are in essence reactive methods and resolve threats only after they emerge (e.g., malware or hacker behavior detection). Crafting a comprehensive risk prevention scheme based on the constantly changing nature of the IT-OT converged environment is key to risk mitigation in the modern industry.
Simply put, preventive risk mitigation is a security approach designed to prevent the exploitation of recognized threats before they occur.
The goal is to ensure production continuity without any failures caused by cyber threats. Ideally, the scheme continuously monitors the production’s attack surface, identifies security gaps, and prioritizes the best mitigation actions based on their potential impact and available resources.
2. Orchestration and automation
In Industry 4.0 environments, IT-based services are connected directly or via proxies to the production floor. Maintaining a minimal IT-OT attack surface in today’s dynamic threat landscape requires continuous security monitoring. When done manually, this is an uphill battle, data overload leads to alert fatigue and hinders resilience.
Automating the security processes overcomes the shortcomings of manual operations, enabling effective and efficient responses to changes in the OT environment and related risks.
Since well-connected systems are more receptive to automation and scale, the connection and coordination between disparate security tools, teams, and infrastructures play a central role in security automation.
This process is typically referred to as ‘Security Orchestration, Automation, and Response’ (SOAR). Some of its benefits include a unified cyber risk overview, accelerated mitigation, and remediation processes (i.e. automated playbooks), as well as standardization and improvement of the operational security posture.
3. Supply chain risk management
Lessons learned from past incidents including the aforementioned HAVEX; different parties in the supply chain can potentially be the source of devastating attacks or amplifiers of ongoing ones.
In most industries, suppliers and vendors are frequently involved in the production floor’s digital services, operations, or maintenance. In many cases, they receive access through the internet, which enables them to directly connect to the production floor, normally without any monitoring and with minimal scanning of the inbound traffic. Additionally, when a new or repaired OT asset is introduced to the production floor, it is done with little, if at all, risk assessment. This situation puts the production in danger and may compromise the entire production floor.
When carrying out digital transformation, a supply chain risk management strategy must be in place. Companies need to address both daily connectivity risks as well as the occasional introduction of a new line, machine, or other OT assets to the production floor.
4. The four-eye principle (reality check)
Upon introducing the preventive automation and orchestration security measures, many of the processes will be handled in a semi-autonomous manner. To test the real-world effectiveness of security, it is recommended, on a periodical cycle, to test security operations from a hacker’s perspective, using a hands-on penetration test by red team experts.
Establishing a validation mechanism like the four-eye principle is important to ensure that the security implementation (i.e., technology, processes, and competence) is aligned with the relevant risks.
Penetration testing does much more than simply validating the successful implementation of the OT cyber security strategy. It is a powerful method to assess the overall organizational security resilience and establish a clear understanding of the state of the security posture. Once gaps are identified, a maturity plan needs to be crafted and executed in order to mitigate the newly identified risks.
5. Production continuity plan
Eventually, even when the best-known security measures are carried out to perfection, a breach may still happen. Once an incident emerges, time is critical to reduce the potential impact and return to complete competence.
A well-trained team, using a prepared playbook, needs to be available in order to restore the operational integrity of the OT network without sacrificing its safety conditions.
The following three steps will help the Incident Response team to considerably reduce the costs associated with cyber incidents:
- The team should take immediate responsibility for containing and eradicating the threat.
- Locating the root cause of the problem and restoring the production floor to its last ‘good’ status from a ‘safety deposit box’.
- Creating a plan to amend the security gaps that allowed the attack to happen.
Survival of the digitally fittest
To stay competitive in today’s global market, industries are forced to change their air-gapped ‘medieval fortress’ philosophy and introduce innovative digital technologies.
To strive in this new reality, while maintaining the production safety and effectiveness, a forward-looking cyber risk management concept must be adopted. Incorporating the five elements into industrial security operations will enable industries to safely move forward and embrace the new digital opportunities presented by Industry 4.0.
Recent Posts