We recently announced that our RAM² - our OT-IoT digital and cyber risk management platform – integrates the MITRE ATT&CK for ICS framework in its “analyst-in-a-box” capability. In this post, we’ll take a quick look into what MITRE ATT&CK is, and why we felt it was important enough to tie so closely to our solution.
What are MITRE, MITRE ATT&CK and MITRE ATT&CK for ICS?
- MITRE is a leading non-profit research and development organization, responsible, among other domains, for creating and maintaining the well-known Common Vulnerabilities and Exposures (CVE) database.
- MITRE ATT&CK is an open knowledge base of adversary tactics and techniques based on real-world observations. Widely-used in the private sector, government, and in the cybersecurity product and service community – the MITRE ATT&CK knowledge base is the foundation for development of threat models and mitigation methodologies.
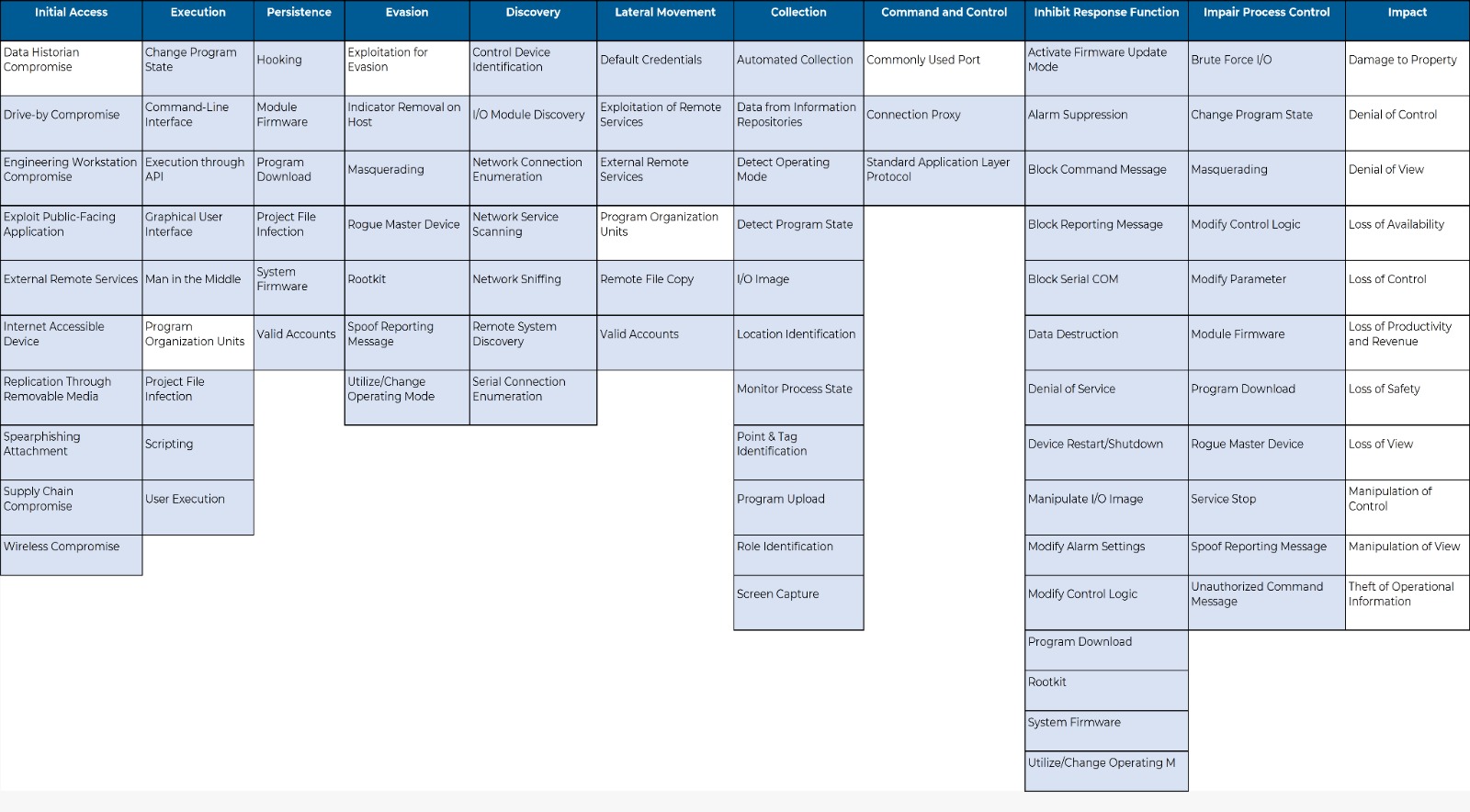
- The MITRE ATT&CK for ICS framework is a knowledge base of tactics and techniques commonly used by adversaries targeting industrial networks. The MITRE ATT&CK ICS Matrix defines 11 top-level categories representing a threat actor’s tactical objectives when attacking ICS environments. For each tactic, the Matrix lists the techniques adversaries commonly use to achieve that tactic.
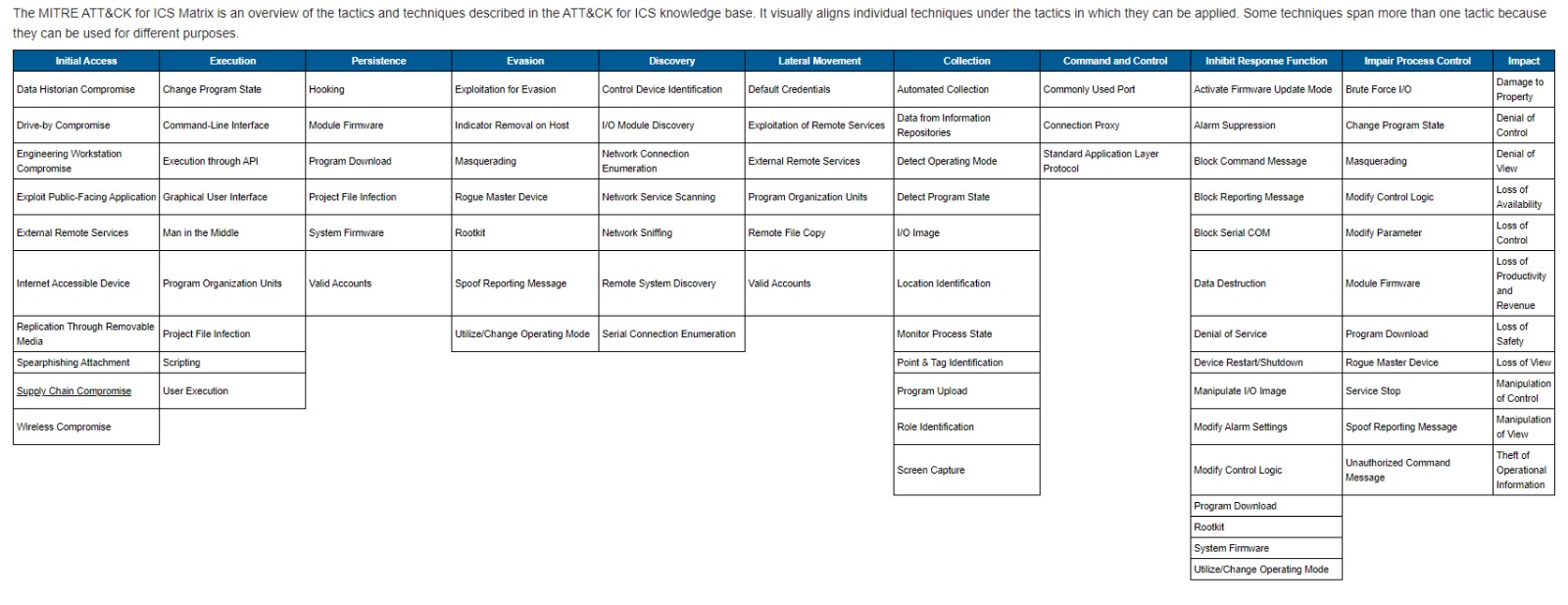
What is MITRE ATT&CK for ICS Used for?
Industrial cybersecurity stakeholders can use the MITRE ATT&CK for ICS framework to develop potential asset failure scenarios, perform testing through red teaming or adversary emulation, assess defense gaps, enrich threat intelligence and improve defenses. It can also be used to educate teams and decrease the knowledge gap between operations and cybersecurity teams.
The problem is that – as helpful as the Matrix is – applying MITRE ATT&CK for ICS is still largely a manual endeavor. For example, you can map event logs with Malware Archaeology’s MITRE ATT&CK Logging Cheat Sheet, which helps you map different events to MITRE ATT&CK techniques. But it is a highly time-consuming operation, and can only identify techniques that already triggered log-generating security events - overlooking many other techniques that attackers might use.
Some traditional security products, such as antivirus and IDS, already map data to various MITRE ATT&CK frameworks. While this is a good start in improving an organization’s detection capability, it does not provide full visibility of network and system security gaps. For example, we used MITRE’s mapping of existing detection methods to calculate that an IDS solution can at best cover 47% of the MITRE ATT&CK for ICS Matrix, and an antivirus solution only up to 26% - leaving a significant portion of potential adversarial activity out of the detection loop altogether.
This is why we decided to integrate the MITRE ATT&CK for ICS into our OT-IoT digital and cyber risk management platform, RAM2 Cybersecurity Platform.
Snapshot: MITRE ATT&CK for ICS and RAM2
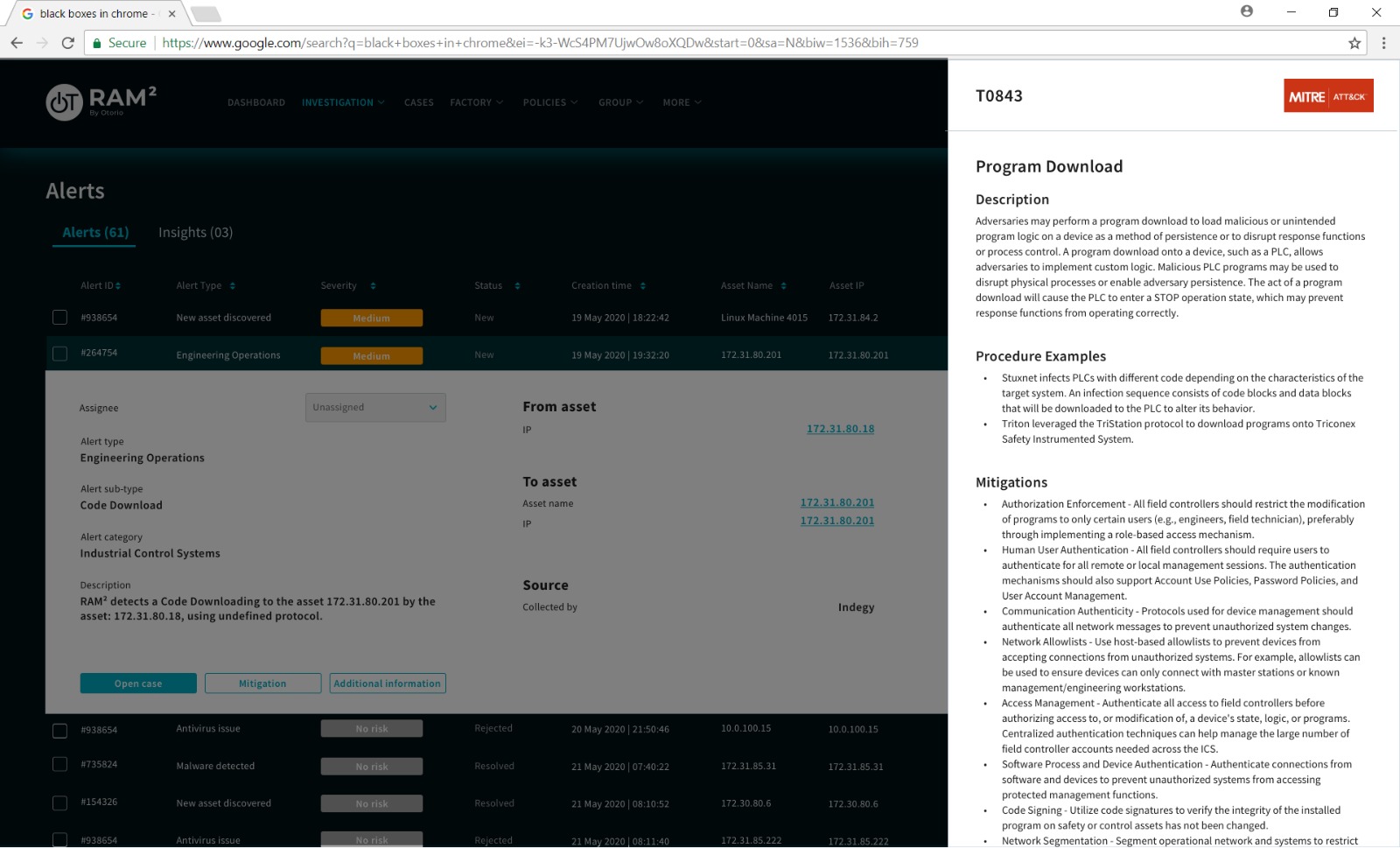
RAM2 integrates the MITRE ATT&CK for ICS framework in its “analyst-in-a-box” algorithm. This means that RAM² maps alerts from its own built-in sensor and from various data sources like EDRs, intrusion detection systems, firewalls, and more to MITRE ATT&CK techniques - enriching event data with the MITRE ATT&CK for ICS intelligence. The result is an 83% coverage of the MITRE ATT&CK ICS matrix.
Then, RAM² correlates events into meaningful adversary intent insights and offers clear mitigation instructions, created with the unique industrial environment in mind.
MITRE ATT&CK For ICS - The Bottom Line
The MITRE ATT&CK for ICS framework is a valuable addition to the security analyst toolbox. Yet like any knowledge base, it is only as powerful in the real world as it is applicable.
For the first time, RAM² turns the MITRE ATT&CK for ICS framework into actionable insights. This makes analysts’ jobs easier and more efficient by providing automatic research-based correlations and allowing users to see security events in the context of adversarial intent – maximizing the amazing potential of MITRE ATT&CK for ICS.
Get the full report to learn more.
Recent Posts