The OTORIO attack graph is a specialized OT network graph that focuses on cybersecurity and represents the potential attack paths and vulnerabilities within the network. It aims to identify the various ways an attacker could move through the network to compromise critical assets. The attack graph is based on a powerful, AI based engine that extracts insights based on network topology and traffic flow. Part of the attack graph engine deduces asset importance automatically based on asset information, network traffic, and topology.
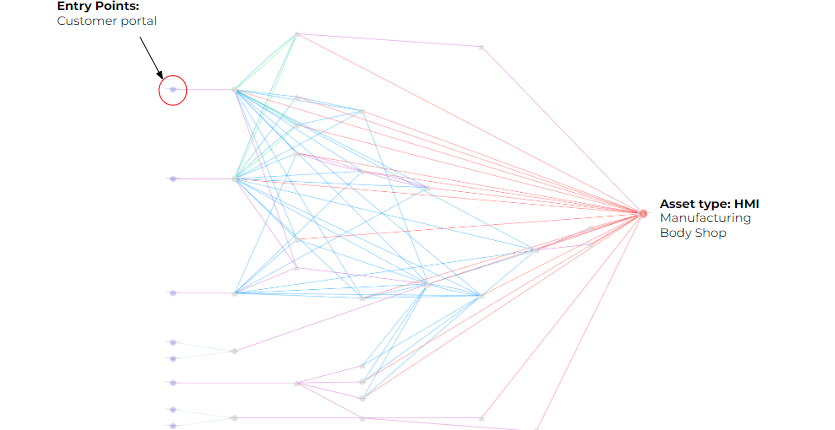
The challenges with this approach is that, even with a powerful algorithmic insight deduction mechanism, the number of insights and posture improvement action items produced is very high. The prioritization required in order to decide where efforts should be spent is based on a topology aware risk assessment algorithm that is used to calculate the risk imposed at different junctures in the network. This helps to localize efforts in high risk areas.
To effectively identify high-risk areas, it is crucial to assess risk considering both the operational and business context. Otorio offers a comprehensive set of features that allow organizations to identify and prioritize critical assets from a business perspective. This enables the organization to focus their protection efforts within the attack graph analysis.
A distinct advantage of Otorio’s solution lies in its unique approach to categorizing the business impact of assets. Assets are classified based on different types of impact they have on the organization. For example, the loss of an asset due to cybersecurity threats may impact business safety or result in financial losses. This categorization empowers operational teams to align their focus with business objectives rather than just network topological areas.
Incorporating compliance requirements into the attack graph analysis is a critical aspect of Otorio’s cybersecurity approach. FOr many OT organizations failing to meet compliance requirements can result in severe legal and financial consequences. Otorio’s attack graph addresses this challenge by integrating features that capture compliance requirements and regulations relevant to the specific industry and organization. By doing so, the attack graph considers potential exposure to regulatory violations in its network visualization and assessment.
Another valuable aspect of Otorio’s attack graph is its adaptability to cater to specific needs of operational teams. The ability to customize the attack graph based on specific target nodes or potential sources of threat enables visualization tailored to the staff’s specific points of interest. This feature allows operational teams to focus on areas directly relevant to their current objectives or ongoing investigations, enhancing their efficiency and effectiveness in analyzing potential threats.
Otorio’s attack graph presents a versatile and powerful cybersecurity solution for OT networks, representing potential attack paths and vulnerabilities. The AI-based engine, combined with automated deduction of asset importance, ensures a comprehensive understanding of the network’s security landscape. The attack graph meets the challenge of information overload with a topology-aware risk assessment algorithm that enables the localization of efforts in high-risk areas. By considering both operational and business contexts, Otorio allows organizations to prioritize critical assets, align protection efforts with business objectives, and mitigate legal and financial risks.
Ensure safe, resilient, and compliant business operations
Follow Us
HQ
ISRAEL
Hamasger St 39, Tel Aviv
USA
260 Ainslie St, Brooklyn
Book a Demo


OTORIO empowers operational & security teams to proactively manage digital risks and build resilient operations via a technology-enabled ecosystem.
Platform


