Geschützter Fernzugriff
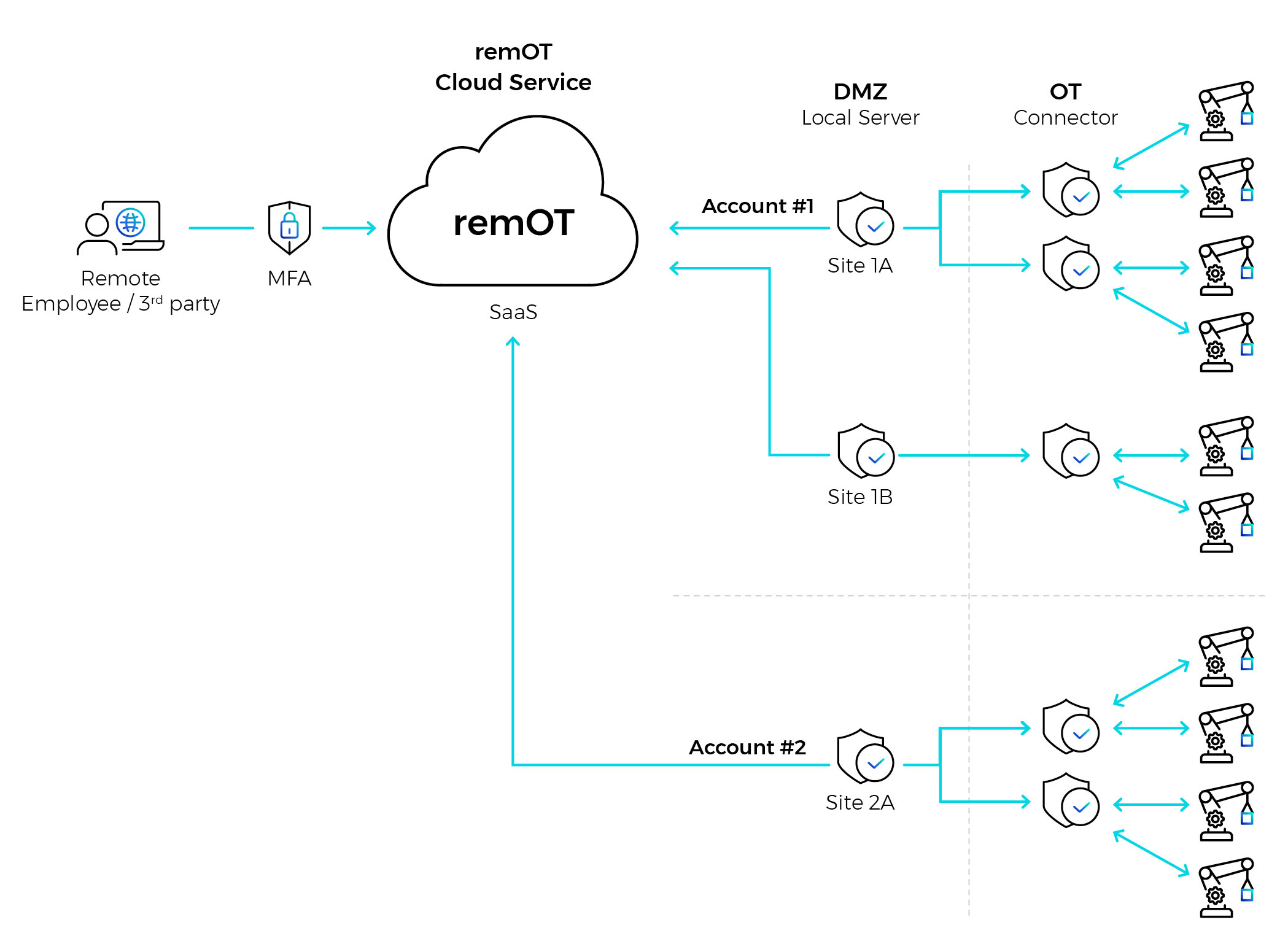
remOTTM von OTORIO bietet einen sicheren, einfachen und vollständig kontrollierten Fernzugriff auf die Betriebsumgebung. remOTTM erfordert keine Agenten-Implementierung, kein VPN und keinen Jump Server. Es vereinfacht die Anbindung von Drittanbietern, Dienstleistern und internen Anwendern an die Anlagen, ohne dabei Kompromisse bei der Sicherheit einzugehen. Die Lösung lässt sich nahtlos an die Anforderungen Ihres Unternehmens anpassen, während die OT-Netzwerksegmentierung zwischen den Standorten beibehalten wird, und das bei niedrigen Gesamtbetriebskosten (TCO).
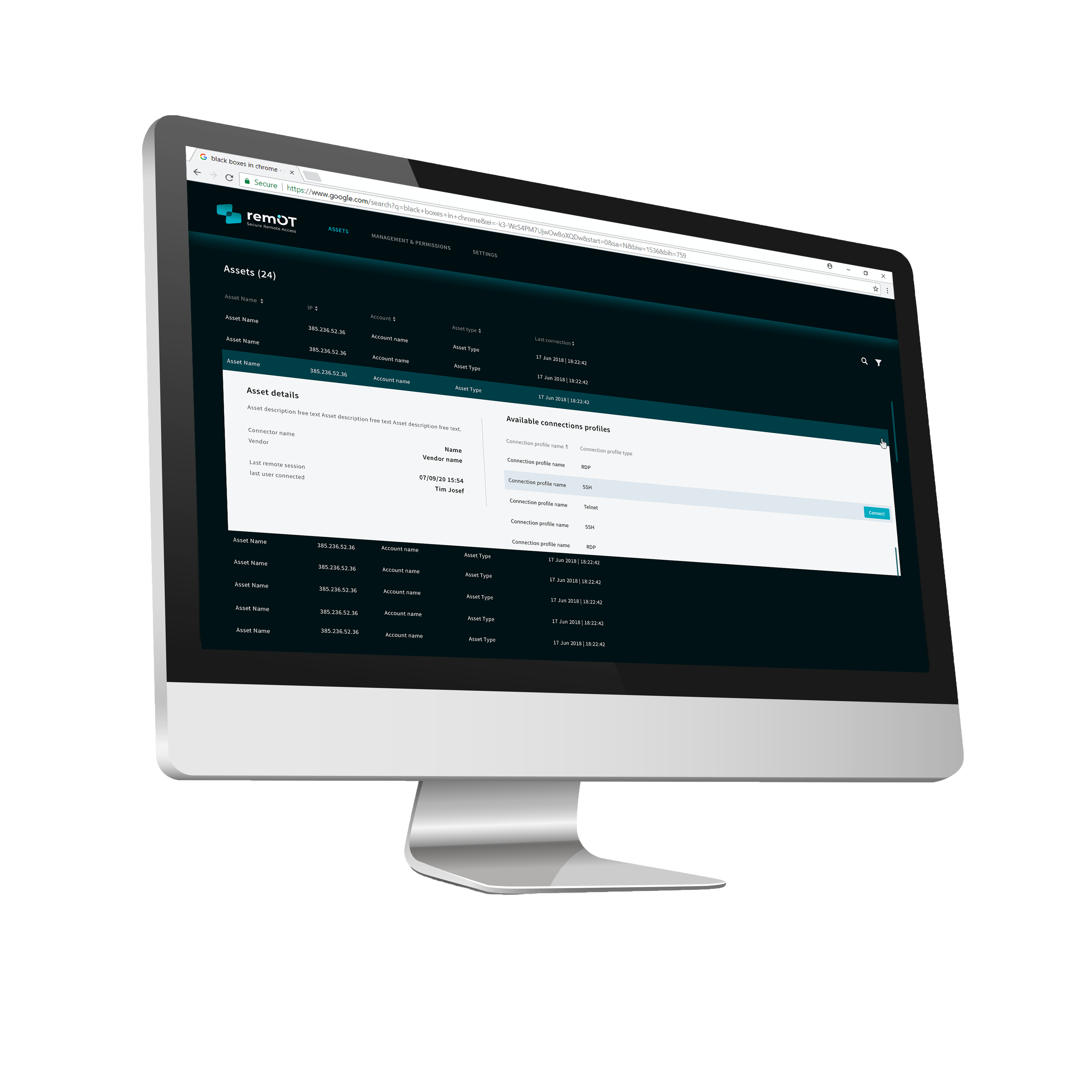
Mit remOTTM wird der Zugriff über eine separate, mandantenfähige Cloud-Kontoverwaltung geregelt und kontrolliert. Der Zugriff wird nur autorisierten Mitarbeitern und autorisierten Dritten auf bestimmte Anlagen gewährt, je nach den Anforderungen industrieller Netzwerke. remOT bietet volle Transparenz für jede sichere Remote-Verbindung.
- Einfache Skalierung mit niedrigen TCO
- Einfache, granulare Verwaltung der Zugriffskontrolle auf Anlagen pro Benutzer.
- Vollständige Kontrolle und Überwachung jeder sicheren Remote-Verbindung
- Sicherheit durch Design für die Anforderungen von industriellen Netzwerken
- Zero-Trust-Zugang für interne und externe Benutzer
- Kein direkter Zugriff auf Anlagen
- Gesicherte Dateiübertragung
- Multi-Tenant-Unterstützung für verschiedene Unternehmen und Organisationen