By David Krivobokov, Research Team Leader
The GhostSec hacktivist group, recently observed targeting Israeli PLC's, continues to demonstrate its ICS hacking skills, and has now turned its support to the recent waves of Hijab protests in Iran.
The group has published several images as evidence of successfully "hacked" systems. These show the use of SCADA modules of the Metasploit framework and a MOXA E2214 controller admin web portal following a successful login. While it is not clear how critical the "breached" systems are, this demonstrates again the ease and potential impact of attacks on ICS systems that have insufficient security controls in place.
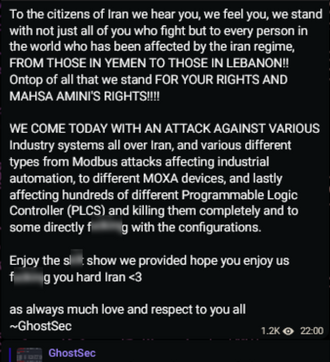
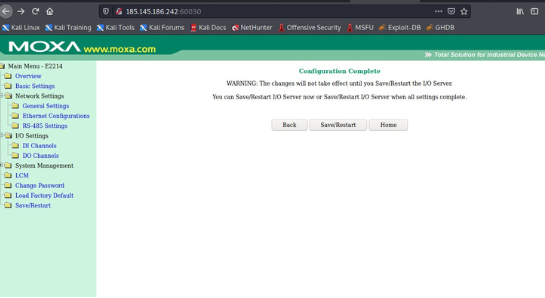
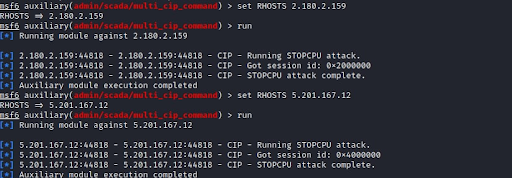
Picture from GhostSec's Telegram showing the use of the Metasploit framework
____________
Here the GhostSec attackers used a framework called Metasploit, which is a very common tool used by security researchers and pen testers. Metasploit is a highly capable and modular framework that allows the execution of a variety of attacks on remote assets. Kali Linux (Linux distribution for hackers) includes Metasploit out-of- the-box, and comes with specific modules for issuing attacks on OT systems. This toolbox gives even novice hackers the ability to cause significant damage to ICS targets. In many cases, they can simply scan the internet for potential ICS targets that have open ports associated with industrial protocols, such as Modbus on port TCP 502 or CIP on TCP port 44818, and then apply the Metasploit SCADA modules or other ICS attack tools on them.
What's most disturbing about this development is that two weeks ago, GhostSec compromised the web interfaces of PLCs, but now they are quickly beginning to look for new open-source tools, and are learning about different OT protocols and their capabilities. The hacktivist group appears to be highly motivated, with capabilities that are growing stronger and stronger each time.
Our recommendation for this episode is the same as last time: make sure not to have direct access from the internet to your OT equipment, especially its operational services. Moreover, invest in minimum cyber hygiene steps such as changing default passwords.
OTORIO's reconOT helps critical infrastructure companies and industrial manufacturers prevent these and similar kinds of breaches that can affect water controllers and PLC devices. It does so via automatic, OT-centric reconnaissance to discover a company's assets and OT security vulnerabilities as a potential attacker would see them.
To learn more, contact OTORIO's OT security professionals.
Recent Posts