By Roni Gavrilov
In an increasingly interconnected world, exposure management serves as a crucial lens through which we can examine the potential entry points and vulnerabilities for cyber threats. Understanding the exposure vectors is essential in fortifying OT systems against modern-day security challenges.
During recent research, the OTORIO team found a disturbing exposure vector that has not been discussed much in the OT security ecosystem - Wi-Fi access points.
The OTORIO team has conducted a comprehensive analysis based on a public “Wi-Fi Access-Points database” called WiGLE, a tool that is free and offers its information for everyone - including potential malicious actors.
During the research, the OTORIO team has determined the following:
- Wi-Fi communication is widely used in different domains of OT, the OTORIO team detected thousands of Wi-Fi access points in manufacturing facilities and critical infrastructures globally. Using publicly available tools - Wi-Fi access points can be easily found geographically, particularly in OT environments.
- According to findings, Wi-Fi access points in critical infrastructure and manufacturing facilities around the world are using weak Wi-Fi encryption modes (such as WEP/WPA) or not using encryption at all.
- Attackers may use this kind of information to geographically locate vulnerable Wi-Fi access points on OT environments, travel to the location and breach the network - using the Wi-Fi as an entry point.

In the Right: Wi-Fi access point record we found in WiGLE
In the Left: Satellite image corresponding to the coordinates in the record
Wi-Fi communication in OT
In the landscape of operational technology (OT), the introduction of Wi-Fi might seem like an unexpected visitor. Yet, as industries increasingly embrace digital transformation (Industry 4.0), the integration of Wi-Fi into OT environments has become not only a possibility but a necessity.
The need for increased connectivity, data visibility, and remote access is driving the convergence of IT and OT. Wi-Fi, with its ubiquitous presence and wireless capabilities, has emerged as a promising solution to meet the increased connectivity demand.
Numerous industries have successfully embraced Wi-Fi integration in their OT environments. From manufacturing facilities and energy grids to transportation systems and logistics facilities, Wi-Fi-enabled OT solutions are revolutionizing operations across diverse sectors.
For example, in the manufacturing sector, Wi-Fi-connected sensors and actuators enable real-time monitoring of production processes, predictive maintenance, and adaptive control, enhancing efficiency and productivity. Additionally, in manufacturing and logistics, Wi-Fi facilitates real-time communication and coordination among Automatic Guided Vehicles (AGVs) and Autonomous Mobile Robots (AMRs), enabling optimized material handling, inventory tracking, and warehouse operations.

Autonomous Mobile Robots (AMRs) in logistics facility
Yet, with these benefits come significant security concerns. Wi-Fi introduces new attack vectors that adversaries can exploit to infiltrate and disrupt critical systems. The inherent vulnerabilities of wireless communication, coupled with the complexities of OT networks, amplify the risk of cyber threats.
Common attacks on Wi-Fi
Wi-Fi technology has become an integral part of our daily lives, enabling seamless connectivity across devices. However, the ubiquity of Wi-Fi also makes it a prime target for malicious actors looking to exploit vulnerabilities and compromise network security. In this section, we'll delve into five common Wi-Fi attacks that every user should be aware of:
1. Man-in-the-Middle (MitM) Attack
One of the most insidious Wi-Fi attacks is the Man-in-the-Middle (MitM) attack. In this scenario, an attacker positions themselves between a user and the Wi-Fi access point, intercepting and possibly altering the communication between them. By doing so, the attacker can eavesdrop on sensitive information such as login credentials, leading to potential identity theft or unauthorized access.
2. Evil Twin Attack
The Evil Twin attack involves the creation of a rogue Wi-Fi access point with a deceptive name that mimics a legitimate network nearby. Unsuspecting users or systems may inadvertently connect to this rogue access point, believing it to be the genuine network. Once connected, the attacker can intercept data traffic, launch further attacks, or disclose sensitive information.
3. Packet Sniffing
Packet sniffing is a technique used by attackers to capture and analyze data packets transmitted over a Wi-Fi network. By deploying specialized tools, attackers can intercept unencrypted data packets containing sensitive information such as authentication credentials.
4. Brute Force Attack
A brute force attack involves systematically attempting different combinations of usernames and passwords until the correct credentials are found, granting unauthorized access to the Wi-Fi network. Attackers often use automated tools to rapidly test numerous combinations, exploiting weak or default passwords to compromise network security.
5. Denial of Service (DoS) Attack
In a Denial of Service (DoS) attack, the attacker floods the Wi-Fi network with an overwhelming amount of traffic, rendering it inaccessible to legitimate users. By disrupting network operations, a DoS attack can cause downtime, financial losses, and inconvenience to users or systems who rely on the network for their activities.
These common Wi-Fi attacks don’t necessarily require advanced skills from attackers, as many of these attacks can be executed using readily and online available tools and techniques, making them accessible to a wide range of threat actors.
However, it is important to know that other types of attacks also exist, such as chipset vulnerabilities, which represent a more complex threat, demanding specialized knowledge and skills from attackers. Additionally, emerging technologies like drones equipped with wireless network-intrusion kits are being utilized for Wi-Fi hacking, expanding the scope of potential threats.
Understanding Wi-Fi attacks is essential for safeguarding your network against potential threats. In the upcoming sections, we'll explore how easy it is to locate Wi-Fi networks in OT environments worldwide, including information such as the network name, network MAC address, encryption type, exact location and more, by using online and publicly available tools and share some best practices and countermeasures to enhance Wi-Fi security.
WiGLE - The SHODAN of Wi-Fi networks
WiGLE, short for "Wireless Geographic Logging Engine," is a comprehensive online database and mapping service dedicated to documenting wireless networks worldwide. A community of users actively contribute to this database by submitting Wi-Fi network information obtained through methods like wardriving or passive scanning.
WIGLE “Wi-Fi scanner” android application, with over 500K downloads
By March 2024, WiGLE counted over 1.2 billion recorded WiFi networks worldwide in its database, with each entry containing essential details such as the network name (SSID), network MAC address (BSSID), encryption type, coordinates, and more.
The platform offers users an intuitive interface to access and analyze this vast database. Through both API and web interface, users can easily search for Wi-Fi networks based on various parameters such as location, SSID, BSSID, and more. The platform provides two levels of filtering options: basic filtering allows users to search using network name (SSID) or network address (BSSID), while advanced filtering, accessible through the REST API, offers additional parameters such as coordinates or encryption type for more precise searches.
WiGLE serves as an invaluable tool for a wide range of users, including researchers, network administrators, and Wi-Fi enthusiasts by providing insights into global Wi-Fi usage patterns. However, on the other hand, it might be used by threat actors as a reconnaissance technique to geographically locate interesting and vulnerable Wi-Fi access points worldwide, some of these access points may exist within OT environments such as manufacturing facilities and critical infrastructure.

WiGLE website
Detecting OT networks exposed by Wi-Fi
Leveraging the REST API filtering options, we wrote a Python script scanning for potentially “high-value” industrial or critical infrastructure environments, highlighting ones configured with weak encryption. Our scanning uncovered thousands of Wi-Fi devices related to industrial and critical infrastructure, with hundreds configured with publicly known weak encryptions.
For detection of these “high-value” networks, we’ve used multiple filters:
- Filter by SSID Name (network name):
a. Looking for OT terms, like ‘PLC’, ‘SCADA’, ’ %waste%water%’, etc.
b. Looking for OT manufacturers names
c. Looking for specific manufacturers or company names - Filter by BSSID (MAC) Prefix:
a. Looking for Industrial / IIoT manufacturers (BSSID / MAC prefixes mapping to vendor names is publicly available).
Filter by SSID Name
We utilized the WiGLE API to conduct queries, applying regex filters that include OT terms to identify networks in operational technology (OT) environments that feature Wi-Fi access points.
Specifically, we filtered the SSID parameter with 21 strings that have clear relation to industrial sites, few examples in the following photo:
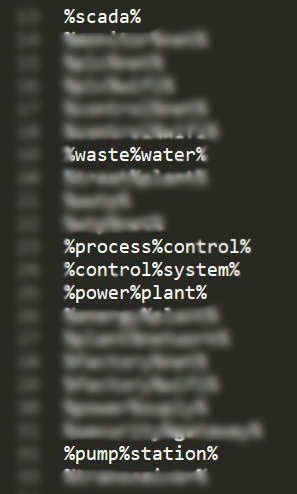
List of regex filters with clear relation to industrial sites
Additionally, we then applied a few more filters over the results in order to remove irrelevant entries and also excluded results older than two years ago, and got approximately 6,000 results.

Thousands of industrial networks SSIDs discovered on WiGLE

Filter by BSSID
BSSID, or Basic Service Set Identifier, serves as the MAC Address of the access point device. By identifying the MAC address, we can determine the vendor through the 'Organizationally Unique Identifier' (OUI) part. This 24-bit number uniquely identifies a vendor.
For instance, if we focus on vendors specializing in manufacturing Wi-Fi access points for industrial usage, such as Prosoft Technology, we can narrow down our search. Prosoft Technology has a single OUI, identified as “00-0D-8D”. By using this OUI as our filter, we can locate all Prosoft Wi-Fi access points in the database. Our search revealed more than 2,700 results (after excluding results older than two years ago).

Geo-locating vulnerable OT Wi-Fi networks
Attackers may abuse this knowledge and travel to specific sites with clear information related to vulnerable encryption, such as WEP/WPA, allowing them to connect directly to sensitive operational areas containing technology that may not be secured by design.

More than 20% of known OT vendor access points are configured with vulnerable encryption

Hundreds of SSIDs with clear relation to industrial sites with vulnerable encryption
Conclusions
In our research, we utilized a publicly available platform called WiGLE, using different filtering methods we discovered thousands of Wi-Fi access points in OT environments.
When we filtered based on the BSSID of a known manufacturer of industrial access points we found that around 20% of them are using WEP and WPA, old Wi-Fi encryption protocols that are no longer considered secure.
To ensure network security, it's crucial to adopt modern and secure Wi-Fi encryption protocols. Here are some recommended protocols:
- WPA3 (Wi-Fi Protected Access 3): WPA3 is the latest standard in Wi-Fi security, offering stronger encryption and authentication compared to its predecessors. It provides individualized data encryption, protection against brute-force attacks, and improved security for open networks.
- WPA2 (Wi-Fi Protected Access 2): Currently the most widely used Wi-Fi security protocol, WPA2 employs AES (Advanced Encryption Standard) encryption and provides robust protection against common attacks when configured correctly.
- WPA2-Enterprise: WPA2-Enterprise utilizes 802.1X authentication with EAP (Extensible Authentication Protocol) methods such as EAP-TLS, PEAP, or EAP-TTLS. It offers enhanced security features suitable for enterprise environments, including mutual authentication and dynamic key management.
- WPA3-Enterprise: Similar to WPA2-Enterprise, WPA3-Enterprise enhances security by utilizing 802.1X authentication with stronger encryption and authentication methods.
While these encryption protocols provide strong security for Wi-Fi networks when configured correctly, it's important to consider other factors such as hiding the network name, using strong password, applying network segmentation, and regularly updating the firmware to maintain effective Wi-Fi security.
Recent Posts