By Matan Doubrushin, Field CTO, OTORIO
A Practical Approach to Utilizing a DID Strategy
Executive summary
If we were to ask you what Defense in Depth is, the answer would be something like
“You need to apply multiple layers of defense to protect your data.” But is it really all that DID is about?
After a thorough analysis of the DID model, we analyzed the philosophy behind it, as well as the practical implementation of it. But most importantly - How to apply it in OT environments?
In our research, we came up with a practical approach to utilize DID strategy in OT environments using up-to-date technologies and threat intelligence.
- The Key takeaways from our research are:
Because of limited resources, it is not possible to implement all layers of security with the same effectiveness. - In order to minimize most risk to an environment, one should put a clear strategy including which layers to implement, but even more important: which layers to ‘sacrifice.’
- The prioritization for the DID strategy should be comprised of a business risk assessment, threat assessment, and countermeasures analysis.
- When dealing with the cyberspace, the threat assessment piece should rely on leading threat intelligence sources like the MITRE ATT&CK Model.
- A new framework by MITRE called D3FEND is a rising star in analyzing effective countermeasures.
Also, this research emphasized what we already know, which is that the most important for OT security personnel is to constantly ask - what is the most important risk I should focus on mitigating tomorrow morning?
Defense in depth and its relevance to OT
Defense in Depth is a very straightforward model that simplifies the strategy of protecting an asset/information with an onion-style philosophy.
The original model puts the data as its center, and obviously, in OT - the center (hence what we are protecting) should be the physical process.
The layers are designed to both put protective mechanisms to stop an intruder from getting into the center but also to put detection sensors to monitor his progression.
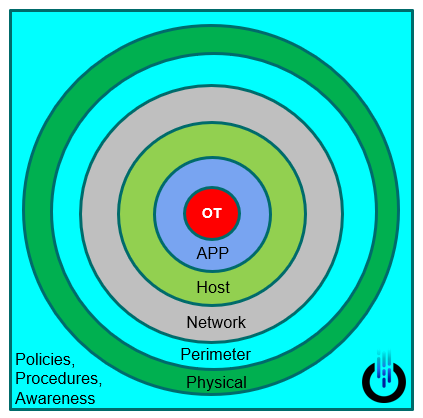
The interesting part of the DID is it’s not a cookbook but rather a holistic approach that tries to calculate the organization’s interconnections, dependencies, and resources to prioritize and give the most efficient tools to deploy a cyber-security strategy.
To apply Defense in Depth to ICS environments, an organization must understand the relationship of intruders (threats) and vulnerabilities to the controls (standards and countermeasures) put in place to protect the operations, personnel, and technologies that make up an ICS.
In a paper from 2016, the DHS published a paper titled “Improving ICS Security with DID Strategies.”
According to the DHS, there are the following elements in DID in the OT environment.
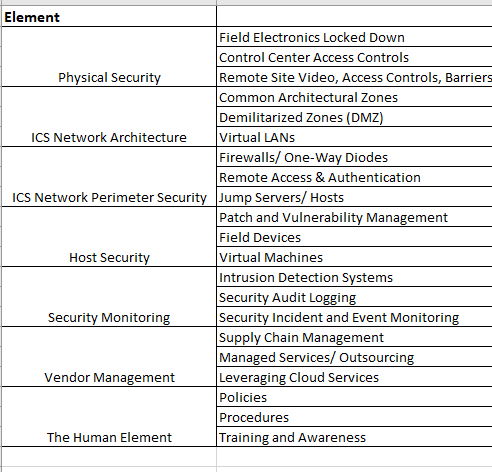
We decided to skip the first two elements, which are “Risk Management program” and “Cybersecurity architecture,” because these are preliminary steps to perform before even looking at the other tactical elements - How one will prioritize tactical steps before performing business risk analysis / establish asset inventory to know what he needs to protect?
But how can we prioritize all of these elements? One metric can be the effort of deploying an element in the network. But other than that - how can we apply threat intelligence prioritization to these countermeasures?
Threat-Intelligence driven approach towards DID in OT networks
MITRE D3FEND is a relatively new (2 years) knowledgebase of cybersecurity countermeasure techniques, unlike MITRE ATT&CK, which is a knowledge base of adversary tactics that only describes what attackers “did” in past attacks.

After analyzing the capabilities of D3FEND, we proposed the following methodology in prioritizing DID for OT environments:
- Perform general risk assessment (Business + Cyber) + Updated Asset inventor.
- Analyze the relevant threats for your organization (Vertical, Geography…) - Using MITRE ATT&CK.
- Have a clear mapping of the corresponding countermeasures for the top threats - Using MITRE D3FEND.
- Prioritize based on all of the above.
Another tool that can help in lining up the relevant countermeasures for your industry is an open-source tool called Control Compass - which queries the MITRE ATT&CK database and others with easy filtering:

After extracting the relevant ATT&CK tactics, we can use a D3FEND extractor in the official D3FEND site to create an Excel sheet with all the relevant countermeasures to the previous query done in the control compass.

After the countermeasures are in a single Excel sheet, it gives the user the ability to practically use the data to draw insights to help prioritize the DID layers for the organization.
Summary
Prioritization of security mechanisms in OT networks is always a challenge, and it is highly recommended to create a plan based on real facts and not on gut feelings. New technologies like MITRE and D3FEND, exist to help and automate the process of choosing the most cost-effective measure for each organization. The support for specific ICS techniques is still limited, but the gap will be closed by the community in the following months.
Recent Posts