One could argue that industrial cyber security is basically suffering from the operational equivalent of Dissociative Identity Disorder (previously known as multiple personality disorder).
The first persona is on-site operational personnel with an engineering background, who are responsible for security maintenance or system hygiene. The second persona is at the corporate level, in the CISO team or a 3rd party MSSP, and comprises security analyst teams with an IT security background usually backed by 3rd party security architects.
In simpler terms, Persona #1 is more proactive and hands-on on continuous production, whereas Persona #2 is inherently reactive involved in breach detection and mitigation. #1 implements a risk avoidance and risk reduction strategy similar to preemptive maintenance processes, while #2 relies on post breach early detection and rapid remediation capabilities.
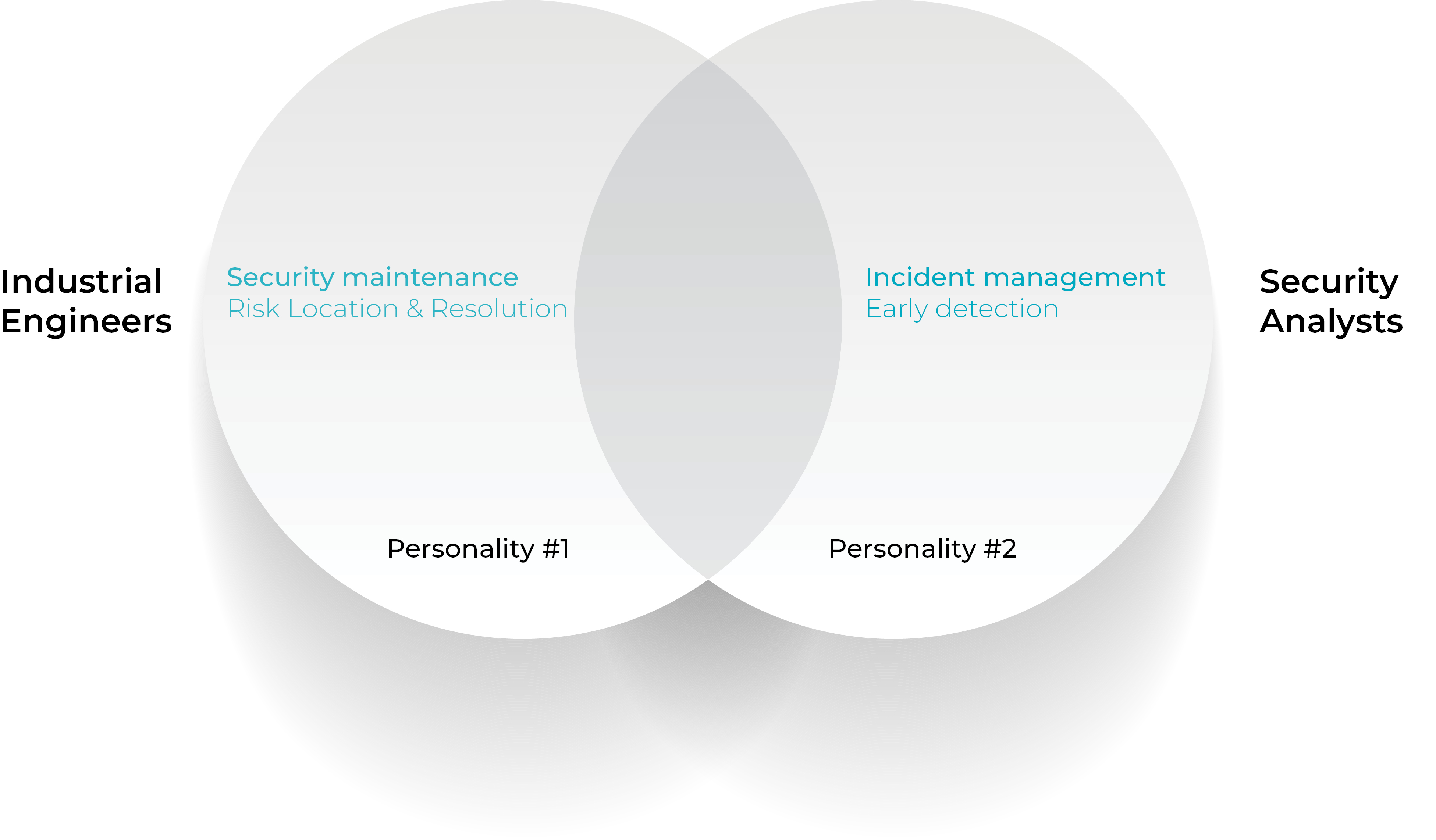
In today’s risk-intensive OT security atmosphere, when safety is at play and down time is not optional, it seems clear that Personas #1 and #2 need to work closely together to prevent (avoid) and mitigate risk across the digital environments. Despite this, until now cybersecurity efforts have focused more on the reactive than on the proactive. And with OT networks under an everly growing attack by sophisticated cyber criminals wielding an arsenal of increasingly sophisticated malware and ransomware – there is not always time to react effectively to cyberthreats and even then the associated damage cost might be substantial.
In today’s volatile cybersecurity climate, the only way to truly mitigate damage is to prevent it. The question is: how can Personas #1 and #2 work together effectively to do so?
The Risk Bow Tie Model
The risk bow tie model is a brilliant/excellent way to visualize how proactive and reactive approaches can work together to eliminate threats that can impact production.
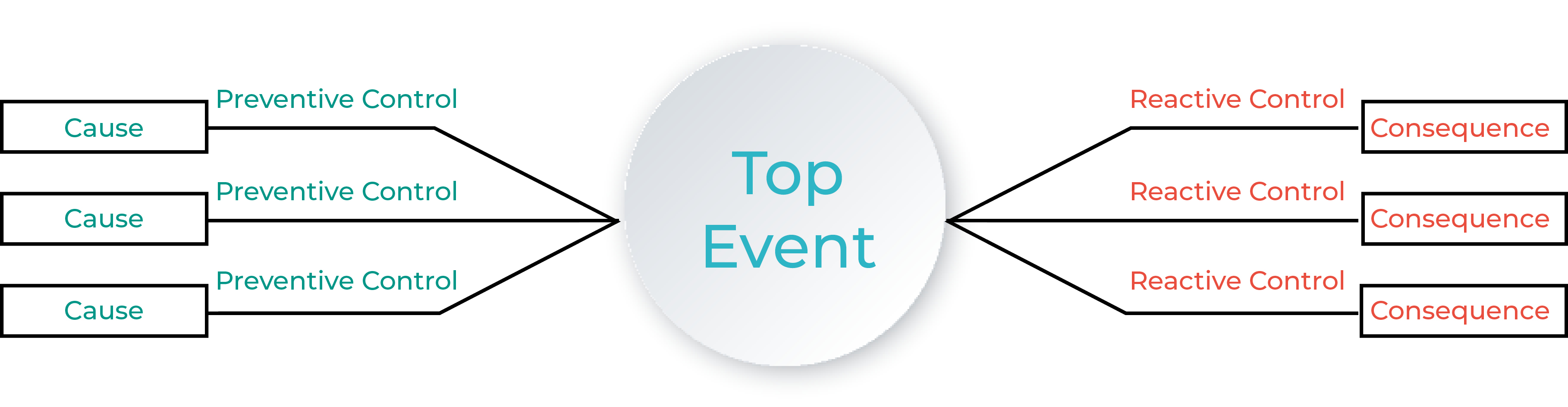
Let’s examine closely the bow tie model. What does each side mean in an OT network security context?
The left side of the diagram shows proactive controls, and is referred to as OpSec. Short for Operational Security, OpSec focuses on proactively mitigating gaps before they become breaches. OpSec incorporates controls that include governance and policy implementation, gap and exposure identification, network architecture and more. True to the domain expertise of Persona #1 above (on-site operational teams), OpSec needs to be implemented with a deep knowhow and familiarity of each facility’s production processes. The reason? OpSec requires a clear grasp of the potential impact of a given threat in situ. This allows the OpSec team to conduct impact analysis that correlates all possible attack vectors to more effectively prioritize preventative measures.
The right side of the diagram shows reactive controls, and is referred to as SecOps, or Security Operations. SecOps efforts tend to revolve around the Security Operations Center (SOC), which focuses on day-to-day missions like monitoring systems, logging, anomaly detection, threat hunting and incident response – all of which are related to reactive and mitigating mechanisms. True to Persona #2, these functions are usually remotely managed at the corporate level or via a 3rd party MSSP.
What Side Does OT Security Demand?
Most OT security solutions on the market today are focused on the reactive SecOps paradigm – the right side of the diagram. The main reason for this phenomenon is that they were conceived from traditional IT security concepts. These solutions detect and respond to security incidents after they happen.
Yet the bow tie model suggests that the focus of effective OT security needs to be spread across the proactive risk reduction or avoidance, similar to preemptive maintenance processes and the reactive post breach detection and mitigation. By combining the two in a hybrid scheme, on-site operational teams are upskilled to manage day-to-day digital and cyber risk reduction, while remote teams continue to monitor ex post facto for incidents and mitigate their impact.
Similar to the contemporaneous trends in IT security, the solution for OT requires adding automation and orchestration capabilities and integrating into risk-based management routines, while enabling a tighter collaboration with off-site cyber security teams.
This will allow Persona #1 and Persona #2 to not only coexist, but also to more effectively meet their ultimate joint goal: a more secure, more productive, production floor and cost effective at the same time.
We at OTORIO had this very concept in mind when we created our RAM² platform. Click here to learn how RAM² can help you in your OT security journey.
¹ https://mynoise.net/NoiseMachines/whiteNoiseGenerator.php
² https://www.juliantalbot.com/post/risk-bow-tie-method
Yair Attar
OTORIO Co-founder & CTO
Recent Posts