Industry
Region
OTORIO’s Solution
Technologies
OTORIO’s Benefits
- Ability to conduct a safe operational security posture assessment without disturbing ongoing operations.
- Improved ROI on pre-existing security controls and solutions by leveraging existing technology investments.
- A comprehensive security assessment report, providing senior management with a full picture of the company’s OT cyber security posture.
- Quick risk mitigation and hardening of site-specific OT network risks and vulnerabilities.
- The company went from only relying upon detection to adopting a continuous, proactive risk-based assessment, mitigation, and management strategy to secure its OT environment.
What is the OT environment in cybersecurity, and why is it different from IT? How can you protect operational technology and ensure ransomware readiness?


In the modern industrial landscape, the convergence of operational technology (OT) and IT has ushered in unparalleled levels of efficiency and productivity. However, such integration has also exposed perilous vulnerabilities, making protecting your OT environment indispensable to ensuring business continuity.
This article looks at the intricacies of the OT environment, highlights its differences with IT, explores the risks OT networks face, discusses required OT cybersecurity measures, and provides insights into safeguarding your technological business environments.
OT Environment Overview
OT refers to hardware and software systems that monitor, control, and manage physical devices, processes, and events in industries such as manufacturing, energy, utilities, transportation, and more. Unlike IT systems that deal with data and communication, OT structures directly manage your core operational processes, making them essential for the functioning of critical infrastructure.
The OT environment encompasses a wide range of devices and systems, from programmable logic controllers (PLCs) and remote terminal units (RTUs) to industrial robots and sensors. They all work in tandem to monitor and control various industrial processes—often in real-time. They’re responsible for tasks such as managing assembly lines, regulating temperature and pressure in industrial settings, and even controlling power distribution in electrical grids.
The Difference Between OT and IT
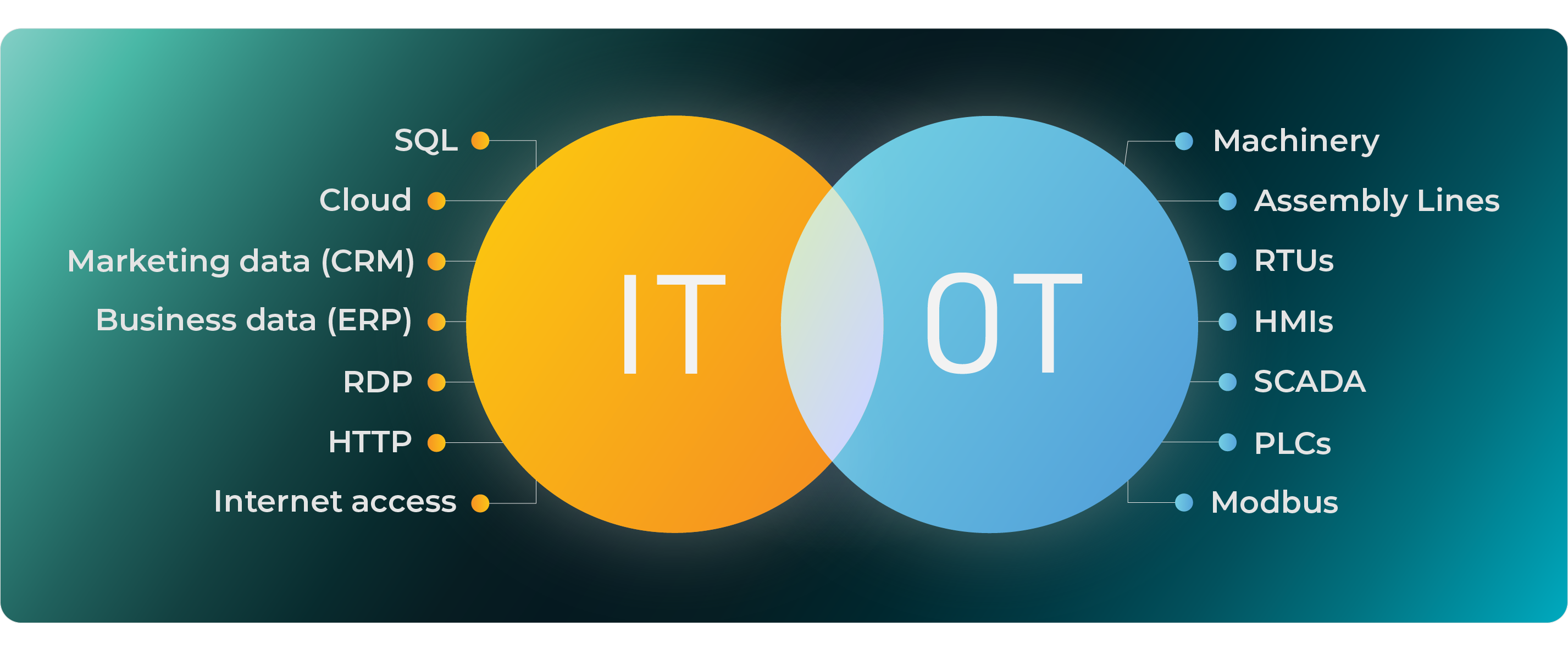
While IT and OT share common technological foundations, they serve vastly different purposes. IT focuses on data management, communication, and computation, supporting administrative tasks such as data storage, email communication, and office applications. Operational technology deals with controlling and monitoring physical processes, making it integral to industries’ core operations.
Such a functional distinction implies that the consequences of an OT environment cyberattack can extend beyond data breaches, thus potentially leading to physical damage, production halts, financial and reputational consequences, and even threats to human safety.
What is the OT Environment in Cyber Security?
The OT environment in cyber security refers to operational technology, the systems, networks, and devices organizations use to monitor, automate, and control industrial processes. OT systems have traditionally been isolated from corporate IT networks, meaning access was limited only to employees with very specific roles.
However, as connected infrastructure and digital transformation have become more common, OT networks are increasingly being integrated into corporate IT systems and the Internet in general. This creates a number of potential cybersecurity vulnerabilities, as malicious actors can use these connections to gain access to sensitive operations equipment, data, and information.
OT Infrastructure Devices
OT environments are typically composed of numerous components, including Programmable Logic Controllers (PLCs), Distributed Control Systems (DCSs), Human Machine Interfaces (HMIs), supervisory control and data acquisition systems (SCADA), Intelligent Electronic Devices (IEDs), and more. These components are connected to physical processes within an organization, such as production lines, manufacturing plants, and other industrial operations.
- Programmable logic controllers – PLCs are ruggedized computers used to automate industrial processes. They control machinery on factory assembly lines, robotic systems, and more.
- Remote terminal units – RTUs monitor and control equipment in remote locations. They collect data from sensors and send commands to control equipment.
- Human-machine interfaces – HMIs provide a visual representation of OT processes. They permit human operators to interact with and monitor industrial machines and processes.
- Distributed control systems – A DCS manages and controls complex industrial processes, such as those found in chemical plants or oil refineries.
- Internet of Things (IoT) devices – Such hardware gathers and transmits data over the internet. IoT devices can monitor equipment performance and environmental conditions in an industrial setting.
- Industrial IoT devices – Designed for industrial applications, IIoT systems provide connectivity and data-sharing capabilities.
- Industrial robots – These machines automate tasks in manufacturing and production to enhance efficiency and precision.
- Pumps, switches, fans, valves, and sensors – Such componentry plays an essential role in various industrial processes and requires monitoring and control for optimal performance.
Why are OT Networks at Risk?
OT and IT system convergence has significant benefits but also introduces new risks. The former were traditionally isolated from the internet, making them less susceptible to cyber threats. But now, the increased connectivity introduced by IIoT and Industry 4.0 initiatives has exposed them to a broader attack surface. Threat actors, including cybercriminals, hacktivists, and even nation-states, have had the potential to exploit vulnerabilities in interconnected OT networks for many years.
The consequences of a successful OT system cyberattack can be catastrophic. For example, targeting a power grid’s OT environment could result in widespread power outages, thereby affecting hospitals, communication networks, and other critical infrastructure. Similarly, an attack on a manufacturing facility’s OT environment could halt production lines, leading to financial losses and supply chain disruptions. Ransomware attacks can also affect OT systems, leading to data loss, service disruption, and even physical damage.
A lack of visibility into OT networks further compounds the challenge of protecting OT environments. Unlike IT networks, they often contain legacy technologies with little or no security capabilities. Consequently, it can be difficult for operators to detect suspicious activity or unauthorized access.
How to Protect the OT Environment and Ensure Ransomware Readiness
Securing your OT environment demands a unique approach due to its distinctive characteristics. It involves a combination of technological, procedural, and organizational measures to mitigate risks and ensure business continuity. Defending against ransomware and other cyber threats requires a comprehensive and multi-layered approach due to the critical nature of industrial processes. Here are several strategies you can employ to best defend your infrastructure against ransomware:
- Network segmentation – Divide your OT network into isolated segments, each with its own purpose and access controls for personnel. This limits the lateral movement of ransomware perpetrators and contains the spread of ransomware if they should succeed in infiltrating a given segment.
- Risk assessment – Identify vulnerabilities and assess the potential impact of cyberattacks on OT systems.
- Access control – Implement strict access controls and strong authentication means, such as multi-factor authentication (MFA), to ensure access and permissions are only granted to personnel based on each person’s specific roles and responsibilities within your organization.
In addition, role-based security establishes a layered defense that aligns with the principle of least privilege, thereby reducing your organization’s attack surface and bolstering the resilience of your IIoT systems against cyber threats. By assigning roles such as administrator, operator, or technician, access to sensitive resources and actions is controlled, thus ensuring each person possesses the minimum permissions required to perform their assigned tasks.
Such a granular approach not only limits potential points of vulnerability but also minimizes the impact of a security breach by containing unauthorized access within predefined boundaries.
- Whitelisting – Use application whitelisting to allow only approved and authorized applications to run within your OT environment. This prevents unauthorized and potentially malicious software from executing.
- Patch management – Vulnerabilities in outdated operating systems and ancillary software can be easily exploited by ransomware. Implement a rigorous patch management process to keep all OT systems, firmware, and software up to date with the latest security patches.
- Network monitoring – Activate continuous monitoring and threat hunting to detect anomalies and potential breaches in real-time. Advanced security monitoring solutions can detect unusual behaviors or patterns indicative of ransomware activity. This includes anomaly detection, intrusion detection systems (IDS), and security information and event management (SIEM) systems. This proactive approach can help catch threats before they escalate.
- Training and security policies – Establish clear cybersecurity policies for OT operations and provide staff training on best practices. Train all personnel—and partners—on cybersecurity best practices and the dangers of phishing and social engineering attacks.
Human error is often an entry point for ransomware. In a recent example, Qakbot malware has been used internationally in ransomware attacks and other cybercrimes that caused hundreds of millions of dollars in losses to people and businesses. Over 700K systems worldwide were primarily infected through spam emails containing malicious attachments or links.
Victims included a critical US government infrastructure contractor and a medical device manufacturer. In announcing the Qakbot takedown, US FBI Director Christoper Wray says such cyber threats are “growing more dangerous and complex every day.”
- Anomaly detection – Employ advanced analytics and machine learning to identify abnormal behavior in your OT environment. It automatically compares each of your OT assets with an extensive database of insecure protocols, known configurations, substandard security practices, the latest CVE data, and other vulnerabilities tracked by component vendors. Equipped in this way, your teams can more effectively identify, prioritize, and remediate potential threats.
- Backup and recovery – Maintain regular offline backups of critical OT data and systems. Ensure they are periodically tested to confirm their integrity and effectiveness for quick recovery, such as in the event of a ransomware attack.
- Incident response plan – Develop a robust incident response plan specific to ransomware. It should outline steps for isolating affected systems, assessing the extent of a breach, and coordinating with pertinent authorities.
- Vendor management – Ensure that third-party vendors and partners follow stringent security practices. Weaknesses in the supply chain can lead to ransomware attacks targeting your operations.
- Encryption – Implement strong encryption for data both in transit and at rest. This protects sensitive information from being easily accessed by ransomware attackers.
By combining these measures and tailoring them to the unique needs of your specific OT environment, you can significantly enhance your defense against ransomware attacks, safeguarding critical operations and minimizing potential damage.
OT Security from OTORIO
Safeguarding your OT environment ensures business continuity in today’s interconnected industrial landscape. IT and OT convergence has brought numerous advantages and exposed critical vulnerabilities. By understanding the unique characteristics of your OT environment and implementing comprehensive security strategies, your business can mitigate risks, protect critical infrastructure, and ensure uninterrupted operations.
OTORIO’s risk-based, full protection approach provides the following OT security best practices:
- Ensures complete visibility of your entire facility
- Performs OT risk assessments across the board
- Secures operational data through 24/7 risk monitoring
- Provides business risk alignment and prioritization
- Improves your industrial security posture through risk mitigation
OTORIO’s unique, proactive technology assesses OT cybersecurity threats by analyzing and visualizing four key components—threat, likelihood, vulnerability, and impact—and provides risk mitigation actions that are prioritized according to actual exposure and potential impact on your operations. The OTORIO platform enables you to achieve an integrated, holistic security strategy for industrial control systems (ICS) and cyber-physical systems (CPS).
In an era of increasing connectivity and digitization, robust OT security is no longer an option but is necessary to ensure your industrial processes' safety, efficiency, and sustainability.
Schedule a demo to learn how OTORIO can help your business.
FAQs:
What are the Cyber Risks with Operational Technology?
Operational technology (OT) represents a unique set of cyber risks from both internal and external sources. OT networks are vulnerable to malicious actors that can exploit systems by infiltrating your network, manipulating data, stealing confidential information, and sabotaging operations.
As a result, organizations must develop an effective OT security strategy to protect their operational assets, people, and processes from these threats.
How should organizations secure their OT environment?
Organizations should take a proactive approach to OT security by implementing an integrated strategy that includes physical security, policy enforcement, advanced risk OT security assessment, risk monitoring, and risk management technologies.
Physical security measures such as access control, authentication methods, and authorization practices can also help protect against unauthorized personnel or malicious actors who could gain access to the network. Organizations can ensure operational resilience by combining these elements into a comprehensive plan.
Why is the threat of Ransomware growing in OT environments?
Ransomware is a rapidly evolving form of malicious software that can disrupt operations and cause significant financial losses. It targets organizations by encrypting files and data, preventing them from being accessed until a ransom is paid.
As ransomware evolves, so does its ability to target OT networks and systems. This means organizations must stay ahead of the game by staying current with cybersecurity tools and OT security best practices to help mitigate ransomware risks.
What are the characteristics of IT and OT devices?
IT devices, also known as information technology devices, are responsible for processing data and handling tasks related to communications, software applications, and day-to-day operations. Examples of IT devices include computers, laptops, servers, routers, switches, firewalls, and access points. OT devices provide critical infrastructure support, such as monitoring factory machines or controlling power grids.
Related Resources:
