Back in September OTORIO Research team published two critical configuration issues on Siemens PCS 7. Today, We’re proud to present a free and open-source tool for detecting and mitigating these issues.
Today there are many efforts made around vulnerability assessment, mainly having tyo do with keeping an updated map of them across the network. In addition, many resources are put into mitigating those threats, by patching the CVEs, or by applying workarounds (such as network segmentation).
While CVE "hunting" is an important process, and should be kept going, there can be simpler ways of exploiting the network. One example is exploiting a default or a misconfigured security configuration on a target endpoint.
We believe such configuration issues must be addressed with (at least) as the same priority as vulnerability scanning and mitigation. We also believe that the defender's role is to mitigate what will most likely be exploited by an attacker. Exploiting a misconfigured Windows share on the network is much easier than applying a complicated CVE exploit. The impact for the attacked company, however, is just as bad.
An Open Source Tool for Siemens PCS 7
Today we’re excited to give something back to the community! We, at OTORIO Research, are publishing a new, open-source capability that we’re hoping would help to improve the security of operational environments.
The tool is tailored to help secure a critical, albeit less known layer in the operational network: the operations layer.
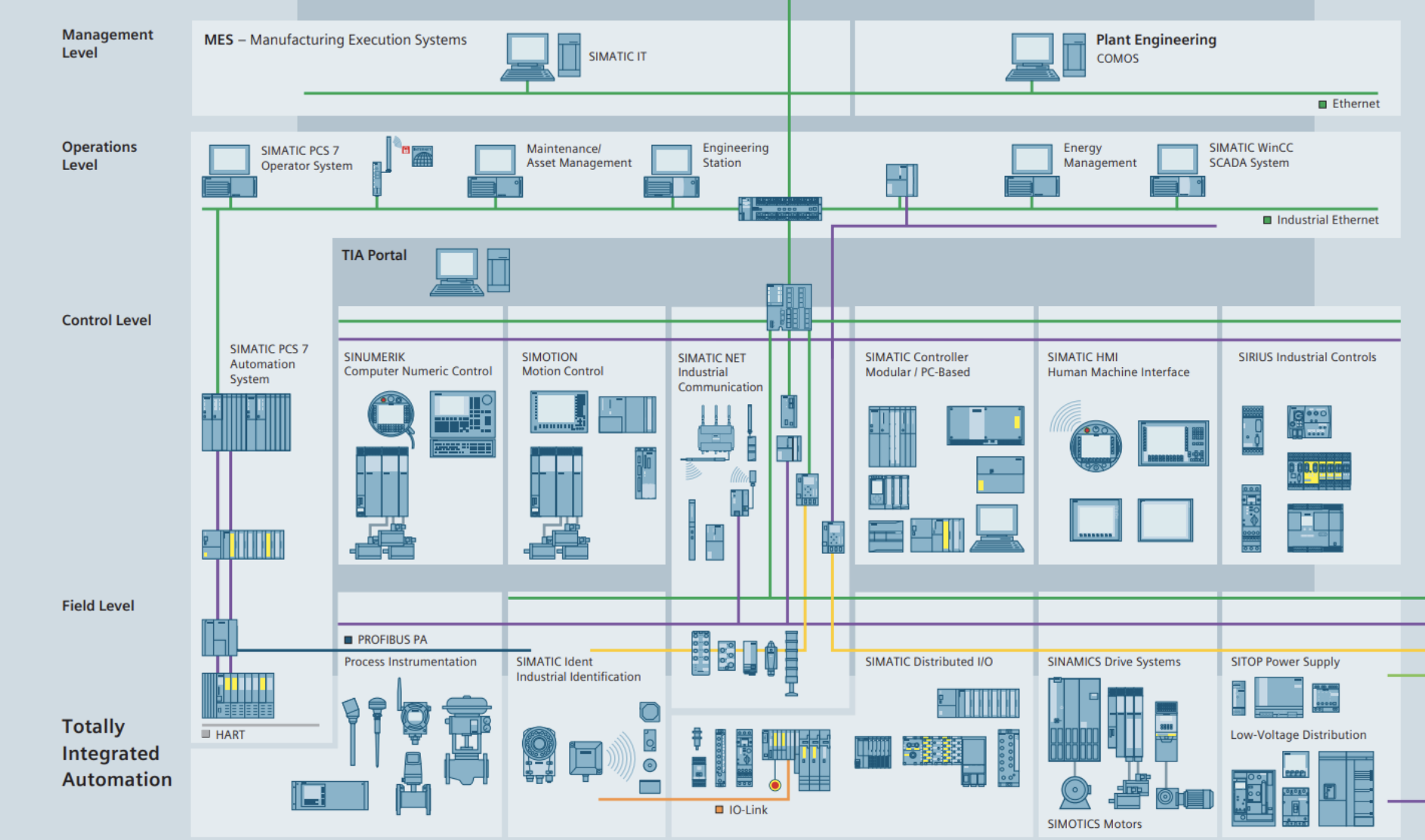
Image source: Siemens PCS 7 Datasheet - https://www.automation.siemens.com/w2/efiles/pcs7/pdf/76/stpcs7_201415_catalog_en_Web.pdf
The PCS 7, DCS environment by Siemens, is one of the most common DCS solutions. Like other DCSs, it contains several components, including the process control, human-machine interface (HMI) and more. The new OTORIO tool can be run on each and every one of the servers in the DCS environment to make sure they are installed with security in mind.
The tool contains 15 security insights, based on dozens of Windows checks, derived directly out of Siemens’s security recommendations. The usage of the tool is as simple as a “double click” of a PowerShell script, which makes it easy to run even for non-technical personnel.
In order to provide backward compatibility, the script was written in Powershell 2.0. Therefore, the script should run on every Windows version since Windows 7 and Windows 2008R2.
The Git contains simple instructions as well as a demo, and a full list of the scans that are being performed alongside with their technical descriptions.
PCS 7 is the system that we’ve decided to start with simply because we have encountered it en-mass in several of our recent customer deployments. But this is just the beginning; stay tuned for tools for more systems (from more vendors) in the near future.
Get the new PCS 7 hardening tool here
Recent Posts