OTORIO Cybersecurity Research team recently discovered two critical issues in the way Siemens’ PCS 7 DCS systems are configured.
The PCS 7 is one of the most common DCS solutions, and like other DCSs, it contains several components, including the process control, human-machine interface (HMI). OTORIO researchers discovered two commonly used configurations in PCS 7 installation process that - if not tended to - can grant privileged access as well as remote code execution on the PCS 7 server to every user.
Impact
DCSs run critical industrial operations around the world. Limiting user access to these systems is crucial for proper network security. Granting overarching user access during installation can enable attackers to breach industrial networks that rely on Siemens and its product line.
According to OTORIO Head of Research, Matan Dobrushin, "We immediately notified Siemens of the two issues and recommend that every Siemens administrator and operator ensure that they did not unintentionally enable the two flaws that my team discovered during PCS 7 installation. Siemens responded immediately and communicated to me that they are taking this report very seriously."
WinCC Configuration Flaw and Recommendations:
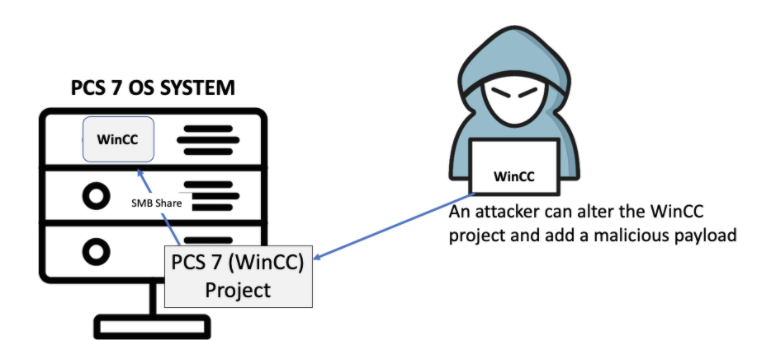
Flaw: WinCC is a PCS 7 component. When an engineer downloads a WinCC project from the engineering station to the OS stations, s/he specifies a network drive - a shared folder - on the OS station. The project is then saved on the shared folder.
It is safe to believe that without clear instructions, a user installing PCS 7 may set access to the shared folder as set to "Everyone" with "Full Control".
Fix: If improperly configured, any user with access to this share remotely can manipulate the project files to achieve arbitrary code execution. Fixing the issue involves limiting user permissions. When installing Simatic WinCC, on the Project Properties section, grant permission only for the user used in the Engineering Station for configuring the project - and not "Everyone". Delete "Everyone" from the shared folders permissions list so this option is not available for future use. Instead of Full Control, choose the most limiting option available that works with your policies. This security issue doesn't require advanced technical skills to exploit, making it more accessible to attackers than traditional CVEs.
PCS 7 Configuration Flaw and Recommendations:
Flaw: The default PCS 7 setup process creates three default user groups. One of the user groups, the Simatic HMI, has access to execute runtime executables. By default, the user in the installation is added to the Simatic HMI group even if s/he is in the administration group.
This default process creates a security vulnerability. A user running WinCC should not be an administrator as this allows the user to potentially harm this and other systems.
Fix: To mitigate the above flaw, create a non-admin user for running the WinCC runtime program and add that user to the SIMATIC HMI group.
Siemens' Statement:
Siemens strongly encourage customers to apply the principle of least privileges during the installation and configuration of the Control Systems and especially to not use any administrative accounts during operation. Both Siemens and OTORIO provide customers with adequate security tools and recommendations such as the Security Manuals [1] and SIMATIC PCS 7 Compendium Part F [2]. Siemens is continuously improving their products and solutions, as well as the respective documentation. Siemens especially thanks OTORIO for raising these specific topics and will incorporate the provided suggestions in the next update of SIMATIC PCS 7 Compendium Part F.
[2] https://support.industry.siemens.com/cs/document/109756871
If you rely on Siemens' PCS 7 and have any questions regarding these two findings, feel free to email [email protected].
Matan Dobrushin
Head of Research
Uri Sade
Cybersecurity Researcher
Recent Posts